If you still aren’t being cautious about which apps you choose to download on your Android phone or tablet, perhaps this latest report will convince you to start taking the warnings seriously. This month, Symantec discovered a new type of Android malware called Sockbot which poses as legitimate apps on Google Play and then adds the devices of users who downloaded the app to a botnet, allowing attackers to create fake ad traffic.
Symantic claims that at least eight Sockbot apps have been identified, each of which has been downloaded between 600,000 and 2.6 million times. The stated purpose of the apps is to modify the skins of characters in Minecraft: Pocket Edition, but behind the scenes, the malware is generating illicit ad revenue.
As Symantec explains on its blog, the Sockbot malware connects to a command and control (C&C) server, opens a socket using the SOCKS proxy mechanism and connects to a specified IP address. Once the connection has been made, a command to connect to a server is issued. Then the app receives a list of ads and the ad fraud begins.
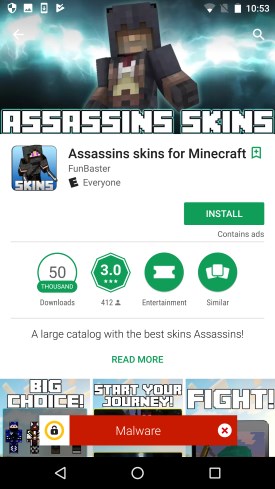
While this is a relatively innocuous use case, Symantec notes that the malware “could easily be extended to take advantage of a number of network-based vulnerabilities, and could potentially span security boundaries.” In other words, attackers could potentially use Sockbot to carry out DDoS attacks going forward.
The good news is that Symantec notified Google of the eight apps on October 6th, at which point the company quickly removed them from the Google Play store. But keep in mind that millions of Android users downloaded these seemingly innocent apps before they were found to be infected. You can never be too careful.








