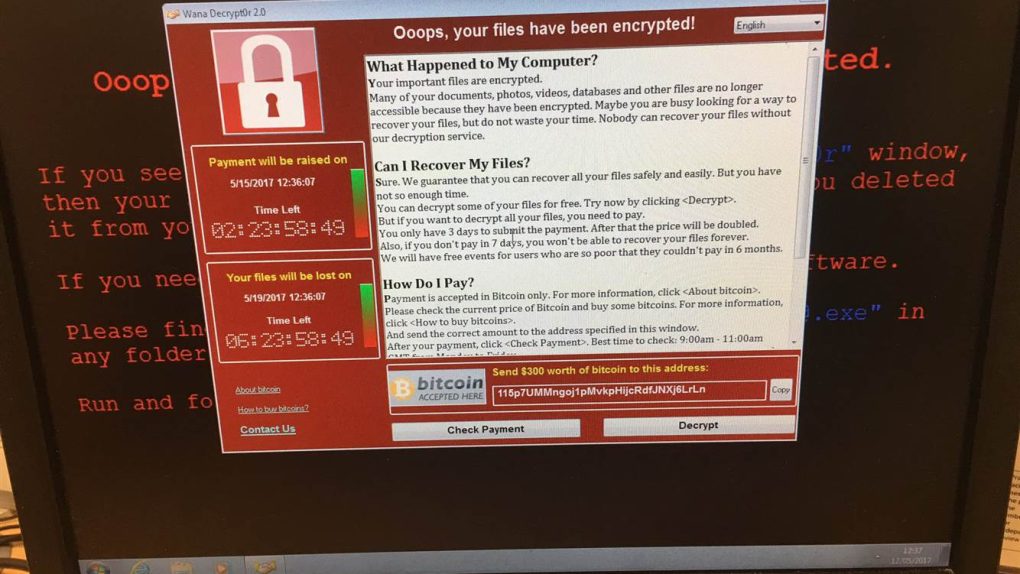
The massive ransomware hack targeting Windows machines across the globe was stopped dead in its tracks by a security expert who inadvertently activated a “kill switch” built into the malware’s code. The ransomware, dubbed “WannaCry”, made headlines on Friday after infecting computers in nearly 100 countries across the world, with Russia and England reportedly seeing the highest number of infections. The ransomware effectively locks users out of their machines, encrypts their files, and instructs them to send $300 worth of Bitcoin in order to reclaim them. The ransomware also states that the $300 payout will increase if a prompt payment isn’t made.
The exploit, which proliferates via email, was reportedly part of a vast treasure trove of NSA hacking tools leaked by a hacking group known as the Shadow Brokers last month. And though the exploit had since been patched by Microsoft, not everyone had updated their software accordingly.
So how did the WannaCry campaign come to an end? Well, a young security researcher — known as malwaretechblog on Twitter — took a look at the ransomware’s code and noticed that it connected to an unregistered domain name consisting of a random string of characters. Out of curiosity, he registered the domain and inadvertently shut WannaCry down.
The following photo via Kevin Beaumont is instructive:

Detailing how the surprise discovery of the kill switch went down, The Guardian reports:
The kill switch was hardcoded into the malware in case the creator wanted to stop it spreading. This involved a very long nonsensical domain name that the malware makes a request to – just as if it was looking up any website – and if the request comes back and shows that the domain is live, the kill switch takes effect and the malware stops spreading. The domain cost $10.69 and was immediately registering thousands of connections every second.
MalwareTech explained that he bought the domain because his company tracks botnets, and by registering these domains they can get an insight into how the botnet is spreading. “The intent was to just monitor the spread and see if we could do anything about it later on. But we actually stopped the spread just by registering the domain,” he said. But the following hours were an “emotional rollercoaster”.
For anyone curious about the nitty-gritty details surrounding malwaretechblog’s ransomware killing adventure, he posted an article detailing the experience on the National Cyber Security Centre website. It’s well worth a read.
I will confess that I was unaware registering the domain would stop the malware until after i registered it, so initially it was accidental.
— MalwareTech (@MalwareTechBlog) May 13, 2017
Well, that went about as well as anything i do does.
— MalwareTech (@MalwareTechBlog) May 13, 2017
It’s worth adding that everyone shouldn’t breathe a sigh of relief just yet. It’s imperative that users should backup their important files, avoid clicking on suspicious emails, and make sure that their operating system software is up to date.
So long as the domain isn't revoked, this particular strain will no longer cause harm, but patch your systems ASAP as they will try again.
— MalwareTech (@MalwareTechBlog) May 13, 2017