Android device owners now have another scam to watch out for as a dangerous malware campaign spreads to new regions. Cybersecurity experts from Cleafy say that they have seen a spike in Android remote access trojan (RAT) infections over the past year. According to Cleafy, BRATA – a malware first discovered in Brazil – has made its way to Italy. Hackers are using the trojan to steal banking details from Android users and then drain their bank accounts.
New Android scam steals banking information
As the cybersecurity experts explain, this new version of the BRATA malware is difficult to detect.
First, the threat actors send an SMS text message containing a link to a website. The text appears to be from the bank. This is a tactic known as smishing (phishing with SMS). If the victim clicks the link, the site they visit will prompt them to download an anti-spam app. The site also tells the victim a bank operator will contact them soon to discuss the app they’re downloading.
This is where BRATA stands apart from other common Android malware campaigns.
Once you visit the site and offer up your information, you will receive a call from a fraud operator. A real person will then attempt to sway you into downloading the malicious app. They will use a variety of social engineering techniques to convince you they work with the bank. Should you fall for it, you might end up installing an app that hackers can use to control your phone.
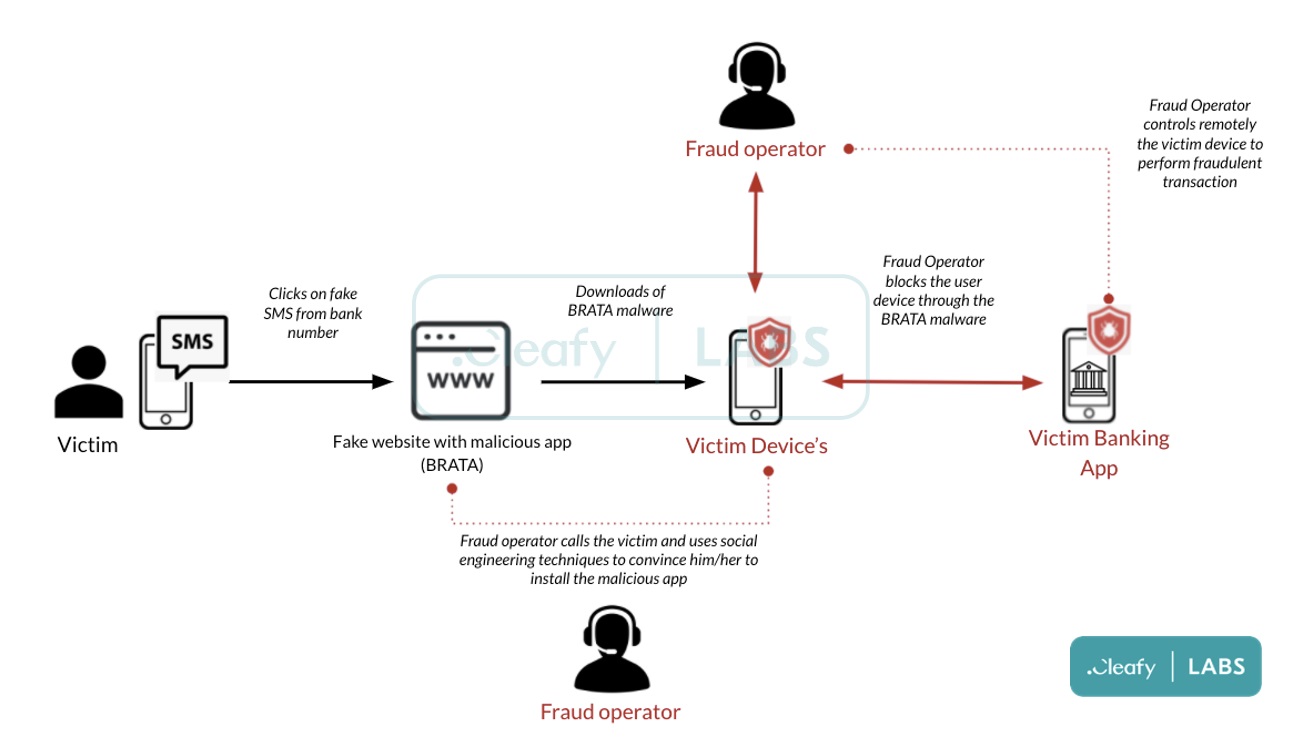
What is BRATA capable of doing to your phone?
Here’s what the BRATA malware is capable of doing after infecting your Android device:
- Intercept SMS messages and forward them to a C2 server. This feature is used to get 2FA sent by the bank via SMS during the login phase or to confirm money transactions.
- Screen recording and casting capabilities that allow the malware to capture any sensitive information displayed on the screen. This includes audio, passwords, payment information, photo, and messages (as shown in Figure 15). Through the Accessibility Service, the malware clicks the “start now” button (of the popup) automatically, so the victim is not able to deny the recording/casting of the owned device.
- Remove itself from the compromised device to reduce detection.
- Uninstall specific applications (e.g., antivirus).
- Hide its own icon app to be less traceable by not advanced users.
- Disable Google Play Protect to avoid being flagged by Google as a suspicious app.
- Modify the device settings to get more privileges.
- Unlock the device if it is locked with a secret pin or pattern.
- Show phishing page.
- Abuse the accessibility service to read everything that is shown on the screen of the infected device or to simulate taps on the screen. This information is then sent to the C2 server of the attackers.
Are you at risk?
The BRATA Android scam first began making the rounds in Brazil in 2019. Cleafy says that the new mule accounts spreading the trojan are mostly coming from Italy, as well as Lithuania and the Netherlands. So, if you live in the US, this specific campaign probably won’t target you. That said, it’s one more scary threat that you should be aware of if you own an Android device.







