If you own any Android devices, you hopefully know to be careful when downloading apps from any source other than Google Play. Unfortunately, even Google Play isn’t always safe, as hackers continue to find new ways to sneak dangerous malware into the Play store. Just last month, security researchers at Cleafy found another seemingly innocuous app on the Play store was actually acting as a dropper for the TeaBot banking trojan.
New malicious app spreads banking trojan
As Cleafy notes, TeaBot is an Android banking trojan that began making the rounds in early 2021. Like similar trojans, TeaBot steals credentials and SMS messages. Initially, the hackers were spreading TeaBot through so-called “smishing” campaigns. Smishing is the practice of sending texts which appear to be from reputable sources requesting personal information, such as passwords and credit card numbers.
But now the TeaBot banking trojan is evolving.
“On February 21, 2022, the Cleafy Threat Intelligence and Incident Response (TIR) team was able to discover an application published on the official Google Play Store, which was acting as a dropper application delivering TeaBot with a fake update procedure,” says Cleafy.
How does TeaBot work?
The dropper is hidden inside of an app called QR Code & Barcode – Scanner. As of March 1st, at least 10,000 Android users have already downloaded the app. As Cleafy notes, the app has many five-star reviews suggesting that it is legitimate. But as soon as you download the app, it will request an update through a popup. Legitimate apps update through Google Play, so this should be the first sign that something is up.
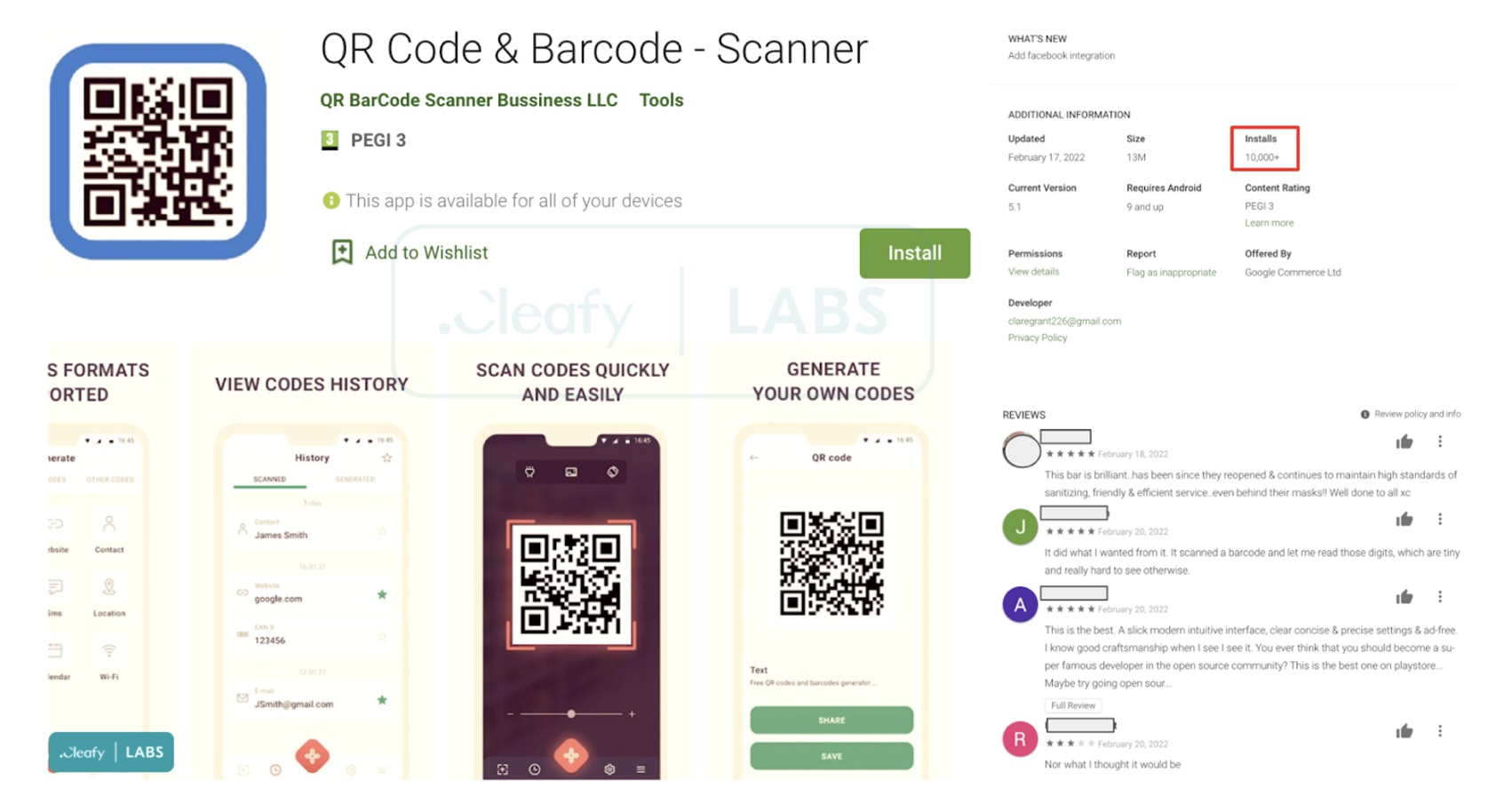
If you go through with the “update,” the dropper will install a second app on your phone. The app, which poses at “QR Code Scanner: Add-On,” is actually the TeaBot banking trojan. TeaBot then starts it installation process on your phone by requesting Accessibility Services permissions. If you grant those permissions, TeaBot can do the following:
- View and control screen: used for retrieving sensitive information such as login credentials, SMS, 2FA codes from the device’s screen.
- View and perform actions: used for accepting different kinds of permissions, immediately after the installation phase, and for performing malicious actions on the infected device.
I shouldn’t have to tell you that you don’t want any app to be able to perform these actions. Much less an app explicitly designed to steal your personal information.
Cleafy goes on to reveal that threat actors using the TeaBot trojan have become even more ambitious. Back in May 2021, TeaBot targeted around 60 applications. Less than a year later, the trojan now targets over 400 apps — a 500% increase. The targets include home banking applications, insurances applications, crypto wallets, and crypto exchanges.
No matter where you’re getting your apps from, you have to stay vigilant. If you aren’t absolutely confident that an app is clean, stay away from it.








