Earlier this month, security researchers at ThreatFabric discovered a dangerous new trojan. They dubbed it Xenomorph due to its ties with the Alien malware, which started to make the rounds in fall of 2020. But while the code resembles that of Alien, the Xenomorph malware is far more capable. According to ThreatFabric, more than 50,000 Android users have installed a malicious application containing the banking app malware. The threat actors behind the malware are reportedly targeting users of 56 different banks in Europe.
Xenomorph banking app malware discovered
As ThreatFabric notes, hackers are always finding new ways to distribute malicious software through the Google Play store. Google is fighting back, but determined hackers always seem to be one step ahead. One recent, nefarious example was the Fast Cleaner app. It claimed to be capable of speeding up Android phones by removing clutter. But in reality, Fast Cleaner was a dropper for the Xenomorph banking app malware.
Here’s what ThreatFabric found after analyzing the application:
Upon analysis, we recognized this application as belonging to the Gymdrop dropper family. Gymdrop is a dropper family discovered by ThreatFabric in November 2021. Previously it was observed deploying a Alien.A payload. From the configuration downloaded by the dropper, ThreatFabric was able to confirm that this dropper family continues to adopt this malware family as its payload. However, contrary to the past, the server hosting the malicious code also contained two other malware families, which were also returned instead of Alien, based on specific triggers.
In addition to distributing the Alien and Exobot trojans, the app also contained a brand new malware family. And that’s how ThreatFabric first discovered Xenomorph.
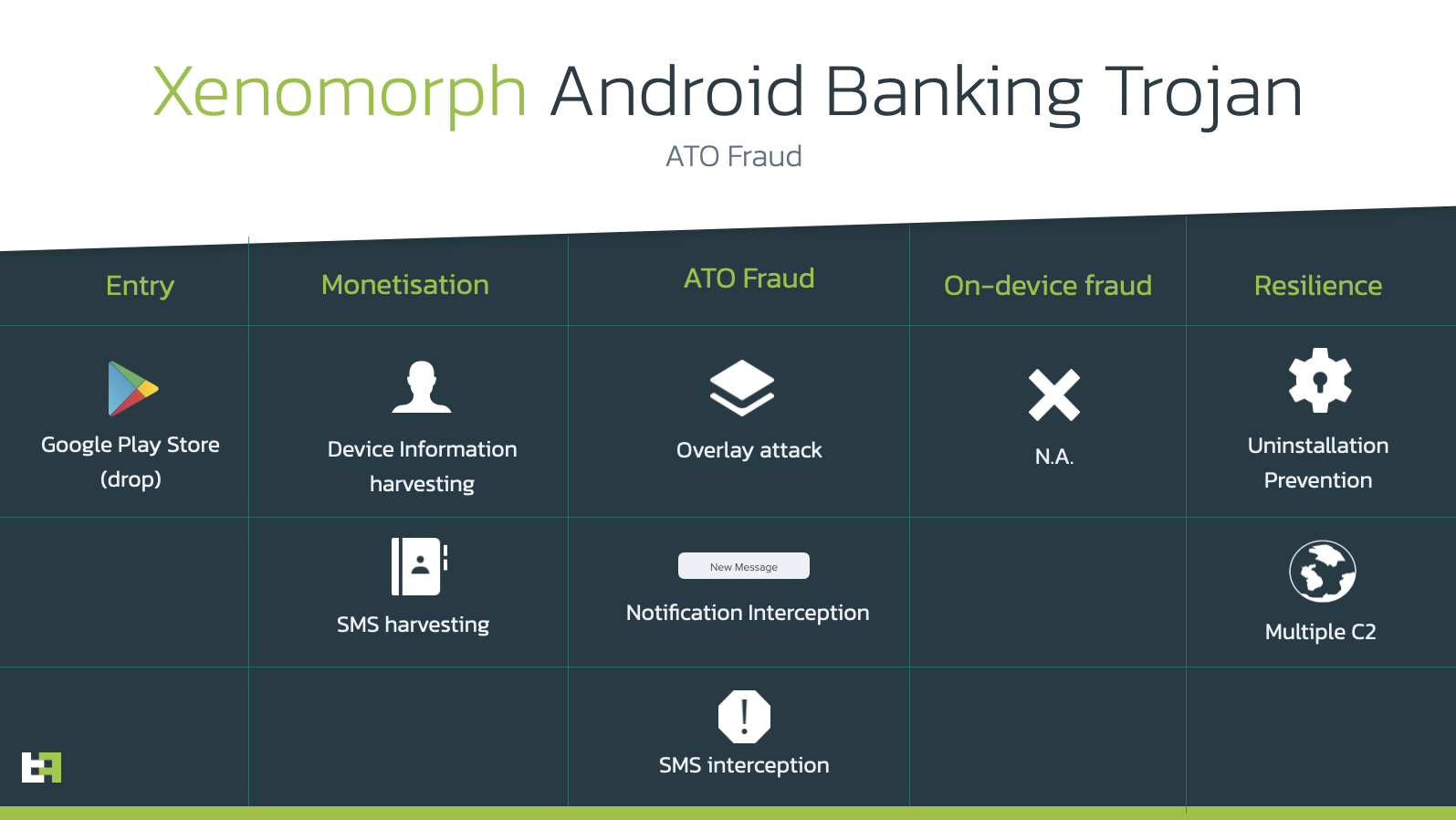
What can Xenomorph do?
ThreatFabric says Xenomorph is still under development, but is already capable of wreaking havoc. The malware’s primary goal is to use an overlay attack to steal credentials for banking apps. It can also intercept texts and notifications to log and use 2FA tokens. ThreatFabric also notes that Xenomorph is designed to be “scalable and updatable.”
“The information stored by the logging capability of this malware is very extensive,” security researchers from ThreatFabric warn in their article, “and if sent back to the C2 server, could be used to implement keylogging, as well as collecting behavioural data on victims and on installed applications, even if they are not part of the list of targets.”
As with most other banking app malware, Xenomorph depends on users giving it access to their devices. Once it infects a device, the malware will ask for Accessibility Service privileges. If it gains those privileges, it can “log everything that happens on the device.”
So far, the malware has targeted users in Spain, Portugal, Italy, and Belgium. Even though it’s still in early stages of development, researchers say it has plenty of untapped potential. Currently, “Xenomorph is capable of abusing Accessibility Services to steal [personal identifiable information] from unaware victims, prevent uninstallation and intercept SMS and notifications.” In the future, it could become even more dangerous.








