The internet can be a very dangerous place if you don’t know how to protect yourself. It’s even more risky if you qualify as some sort of high-value target that hackers would go after with all kinds of cyberattacks. The newest security update from Swiss software developer Proton makes all that abundantly clear.
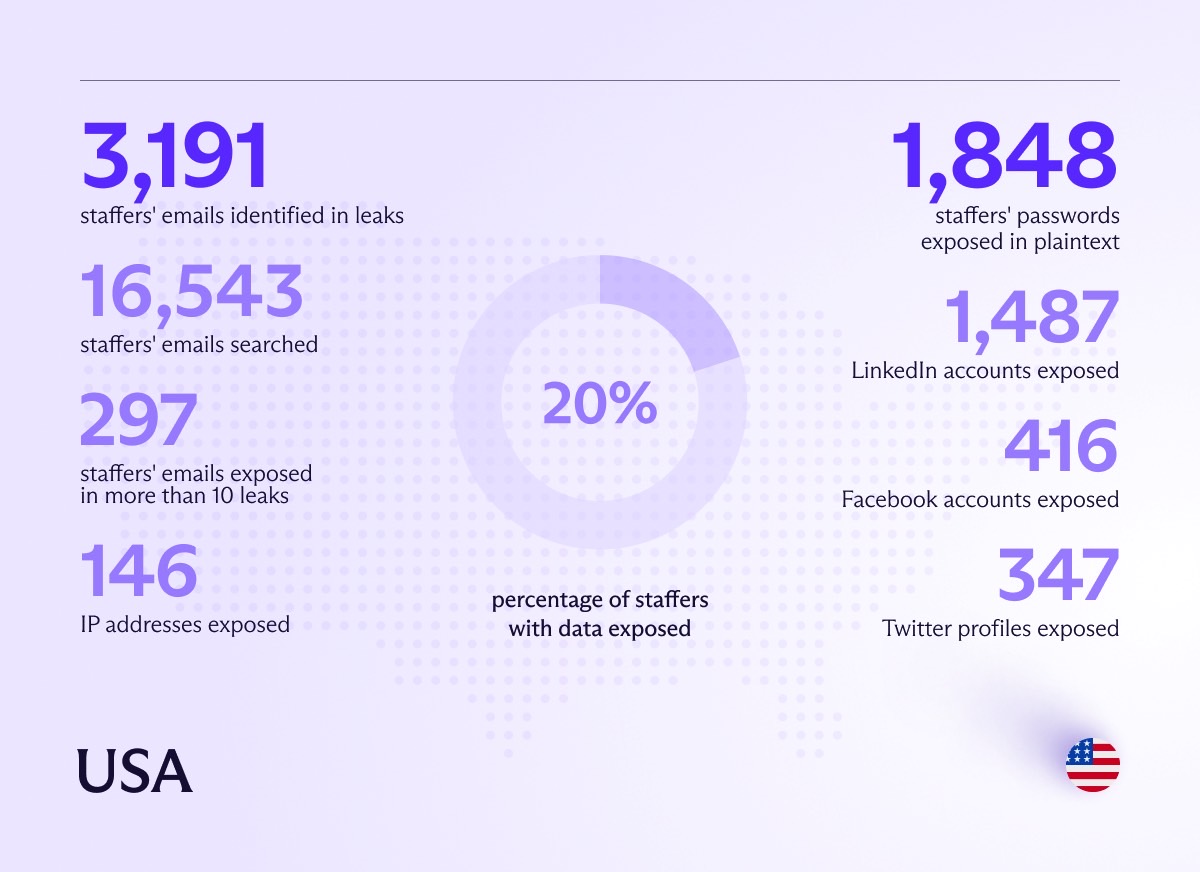
Proton partnered with Constella Intelligence to analyze the security vulnerabilities of US political staffers, finding that nearly 20% of them had personal data leaked on the dark web following various hacks. That amounts to thousands of exposed individuals who work for the US government.
Proton analyzed 16,543 email addresses belonging to US political staffers, finding that 3,191 were at risk. That’s how many email addresses appeared on the dark web following various hacks.
Proton only looked at staffers, as the emails of actual members of Congress aren’t always public. But staffers are an entry point for would-be attackers, as they can have access to plenty of sensitive information, including the kind that needs security clearance.
The research shows that nearly 300 staffers had details exposed in more than 10 leaks.
One person had 31 plain-text passwords exposed on the dark web. In total, Proton found 1,848 plain-text passwords associated with political staffers.
The leaks also included information from social media. 1,487 LinkedIn profiles, 416 Facebook profiles, and 347 X profiles were found in the leaks.
These findings do not indicate that US political staffers were the target of specific spying campaigns. Instead, Proton explains that a bad internet security practice is likely to cause many of these leaks. These staffers used their official email addresses to sign up for various services. This might include “high-risk sites such as dating and adult websites” that might have been compromised in data breaches.
That’s not to say that US government officials aren’t constantly attacked by hackers. Proton says that Washington, DC, has been a prime target for attackers for more than a decade. Hacking attempts can intensify during key election cycles.
Proton advises US political staffers to avoid their work addresses to sign up for third-party services unless absolutely necessary.
Using password managers, like Proton’s own Proton Pass, can improve the security of login data. Password managers also let you save unique passwords for the various online services you might use.
Proton Pass can also hide your real email address with aliases, which will prevent the real addresses from ending up in data spills on the dark web. In addition, Proton offers services like Proton Pass Monitor and the Dark Web Monitoring service that can help you determine whether your data has been exposed.
But this advice is valid for any internet user juggling hundreds of different credentials. I’ve been recommending password managers for years and always do it whenever a new hack comes to light.
I’ve been using Proton Pass together with 1Password for more than a year, and it’s incredibly easy to use. The service has seen various upgrades along the way, including standalone apps for multiple platforms.
Regarding the compromised data from US political staffers, Proton says it has informed all of them. Proton has done similar research on the EU and UK in its security blog, which was updated with figures for the US political landscape. It turns out politicians in those regions might be even worse than Americans when it comes to protecting their official work addresses.








