Google is waging an endless war against threat actors who want to steal our data with malicious apps. At least once a month, the cybersecurity community appears to find a malware campaign threatening Android users. Late last month, researchers from cybersecurity company ThreatFabric found another cluster of dangerous Android malware apps on the Play store. These apps posed as PDF scanners, QR readers, and banking apps. They belong to four different malware families, were distributed over the course of four months, and were downloaded over 300,000 times.
New Android malware apps on the Play Store
As ThreatFabric notes, Google has made strides in keeping Android malware apps off of its app store. A few weeks ago, Google closed a loophole that allowed hackers to abuse accessibility tools to install apps without a user’s consent. But hackers never stop finding new ways to infiltrate the store.
Because Google works so hard to detect malware, the creators of these apps have to find new ways to skirt detection. As a result, the threat actors have been forced to reduce the footprint of dropper apps they create. Rather than upload a blatantly malicious app to Google Play, hackers will instead roll out “carefully planned small malicious code updates over a longer period.”
It’s a longer, more complicated process, but it’s far more successful in avoiding detection. When the researchers initially tested each of the apps on VirusTotal, they came back clean. Over the course of days, weeks, or months, an otherwise innocuous app could become dangerous.
How does the infiltration work?
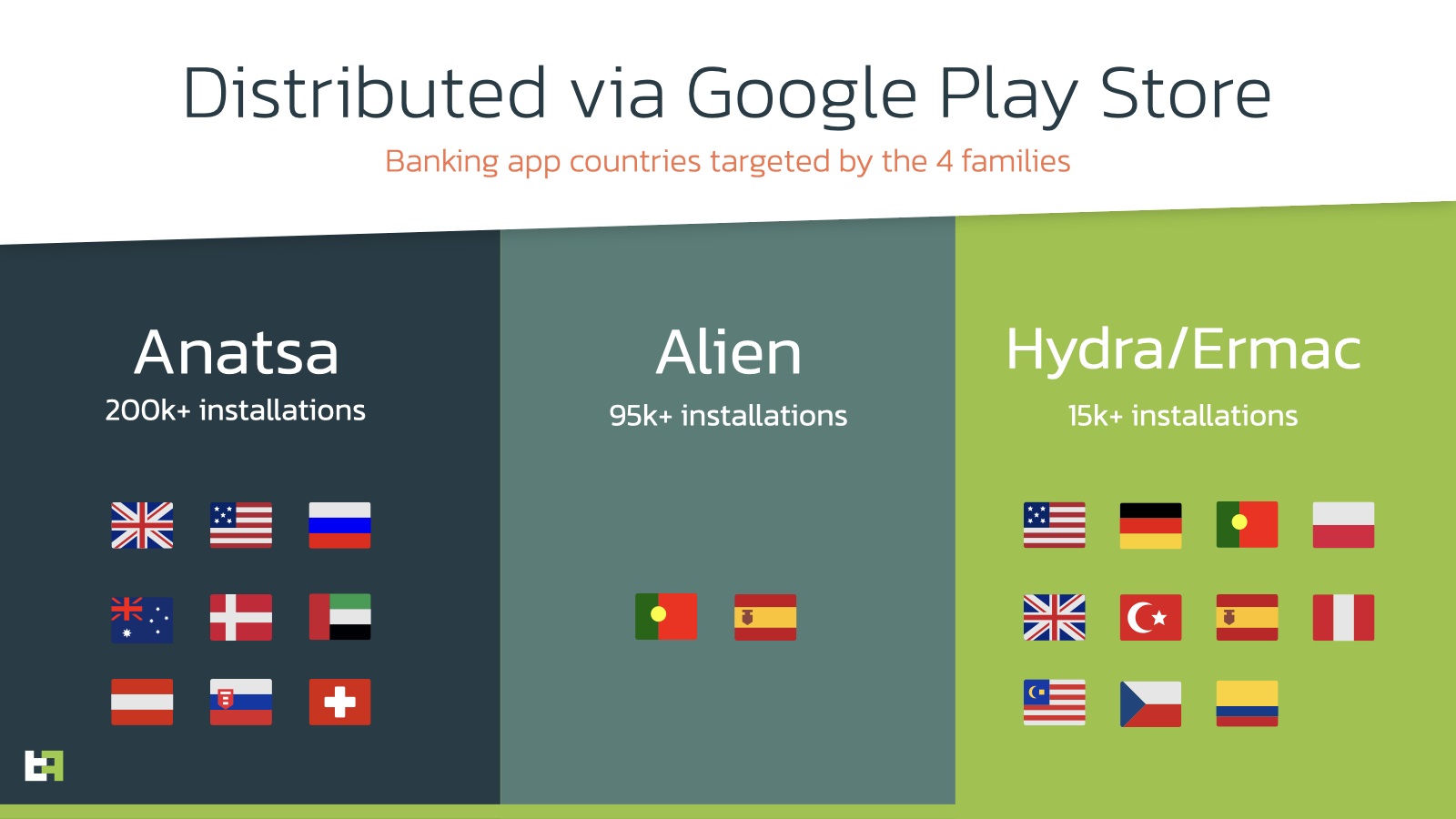
According to ThreatFabric, the banking trojan Anatsa is to blame for a majority of the infections that its researchers uncovered. The team went into detail about how Anatsa infects smartphones:
The process of infection with Anatsa looks like this: upon the start of installation from Google Play, the user is forced to update the app in order to continue using the app. In this moment, Anatsa payload is downloaded from the C2 server(s), and installed on the device of the unsuspecting victim.
Actors behind it took care of making their apps look legitimate and useful. There are large numbers of positive reviews for the apps. The number of installations and presence of reviews may convince Android users to install the app. Moreover, these apps indeed possess the claimed functionality, after installation they do operate normally and further convince victim in their legitimacy.
Despite the overwhelming number of installations, not every device that has these droppers installed will receive Anatsa, as the actors made efforts to target only regions of their interest.
We’ve covered dozens of Android malware apps and campaigns in the past. Often, the apps in question are nothing more than cheap fakes that serve no purpose other than infecting phones. In this case, the apps actually work. If the user is seeing the desired results from their app, they have no reason to be concerned. This is why Google, researchers, and users have to be increasingly diligent when installing apps. Think twice before you download a new app, even if it’s on Google Play.
Head over to the ThreatFabric report to ensure you don’t have any of these Android malware apps on your phone.








