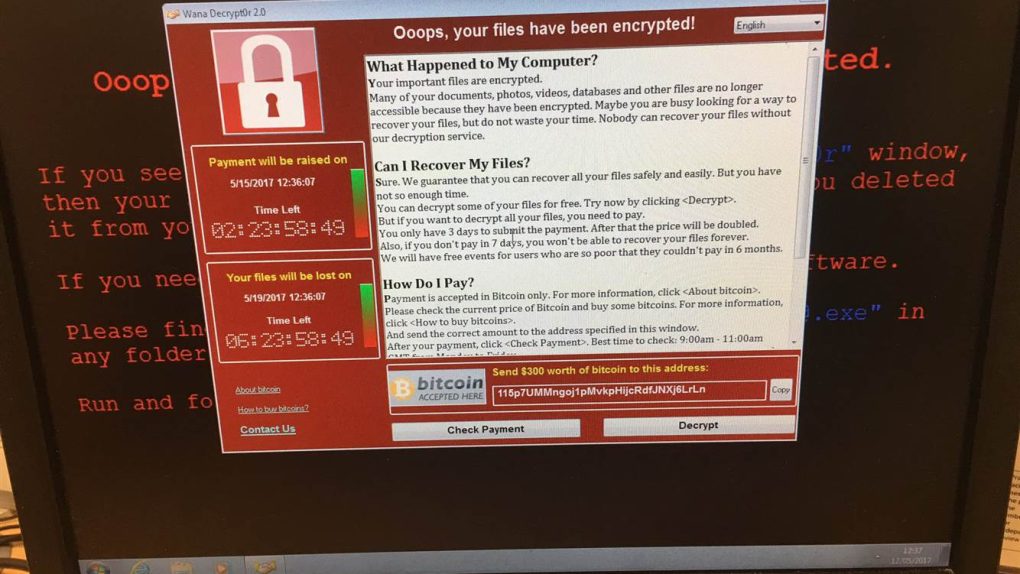
When the WannaCry ransomware took hold earlier this month, it quickly began infecting thousands of machines in a number of countries all across the world. In the process, it even managed to infect computers at the National Health Service in the UK, effectively disabling IT systems at a number of hospitals.
All told, it’s believed that WannaCry managed to infect upwards of 300,000 machines, a figure that could have been much higher had it not been for a security researcher who accidentally stumbled upon the malware’s kill-switch. Incidentally, security researchers, the days following the attack, even managed to come up with a solution for some impacted users, effectively allowing them to reclaim their encrypted files without forking over $300 worth of Bitcoin to an unknown group of hackers.
A few weeks removed from the WannaCry attack, there’s still no concrete proof as to who was behind it. While we know that the ransomware itself was based on an exploit leaked by the Shadow Brokers, it’s believed that the group behind WannaCry is a separate entity altogether.
Early on, there was a lot of speculation, and some evidence, linking WannaCry to the Lazarus group, the same outfit behind the Sony Pictures hack of 2014. Incidentally, there is some speculation that the Lazarus group may be loosely affiliated with North Korea.
More recently, though, an analysis of the language on the WannaCry splash screen has prompted some researchers to point the finger at China. According to security researchers from Flashpoint, there are some interesting data points to be gleaned from examining the specific language and grammar used by WannaCry’s authors.
All told, the WannaCry malware appeared in 28 distinct languages, 26 of which were reportedly put together using Google Translate. Interestingly, though, the WannaCry ransom message in Chinese and English appeared to be written by a human.
Analysis revealed that nearly all of the ransom notes were translated using Google Translate and that only three, the English version and the Chinese versions (Simplified and Traditional), are likely to have been written by a human instead of machine translated. Though the English note appears to be written by someone with a strong command of English, a glaring grammatical error in the note suggest the speaker is non-native or perhaps poorly educated.
…
The two Chinese ransom notes differ substantially from other notes in content, format, and tone. Google Translate fails in both Chinese-English and English-Chinese tests, producing inaccurate results that suggests the Chinese text was likely not have been similarly generated by the English text.
A number of unique characteristics in the note indicate it was written by a fluent Chinese speaker. A typo in the note, “帮组” (bang zu) instead of “帮助” (bang zhu) meaning “help,” strongly indicates the note was written using a Chinese-language input system rather than being translated from a different version. More generally, the note makes use of proper grammar, punctuation, syntax, and character choice, indicating the writer was likely native or at least fluent.
This theory is of course speculative, but it certainly adds an interesting twist to an already engrossing saga. Before the WannaCry ransomware was stopped dead in its tracks, security researchers believe that victims forked over upwards of $80,000 worth of Bitcoin.