Earlier this week,security researchers unearthed two familiar strains of malware specifically targeting Mac users, according to a new report from Ars Technica. While both pieces of malware are admittedly clunky and decidedly unsophisticated, it’s nonetheless something Mac users will want to keep an eye on.
The first piece of malware, interestingly enough, relies on an old technique that malware creators previously used with great success on Windows machines back in the day. Specifically, the malicious code resides inside of Macros that spring into action when a modified Word document is opened and the appropriate permissions granted.
In this scenario, a Microsoft Word document titled U.S. Allies and “Rivals Digest Trump’s Victory” has been making the rounds. When a user opens the document, they are presented with a dialog box allowing them to either enable of disable Macros.
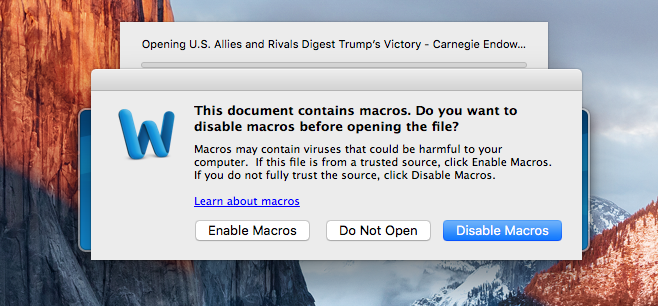
If the user doesn’t opt to disable Macros, a payload will be downloaded and executed from a remote server once it’s determined that the app LittleSnitch is not installed and running.
While it’s still not entirely clear what the malicious code does, it’s clearly easy to steer clear of this relatively ancient style of malware attack simply remaining vigilant and not enabling Macros on a random Word document one finds on the web or curiously receives from a friend.
But as Ars points out, that may be giving end users far too much credit:
As unsophisticated as they seem, malicious macros remain vexingly effective at infecting large numbers of people who should know better. Word macros, for instance, were the initial infection point to the first known hacker-caused power outage, which left 225,000 Ukrainians without electricity in December 2015. Malicious macros also power some of the most aggressive strains of ransomware, including one known as Locky.
Meanwhile, another piece of Mac malware called MacDownloader was recently unearthed as well. Believed to be developed in Iran, this particular piece of malware targets defense industry officials spear-phishing emails containing links to ostensibly legit websites. Once there, visitors are prompted with a dialog box asking them to update their Adobe Flash Player. If they proceed, the malware is designed to steal a user’s credentials via a “fake system login” and then gets to work.
In parallel, MacDownloader harvests information on the infected system, including the user’s active Keychains, which are then uploaded to the C2. The dropper also documents the running processes, installed applications, and the username and password which are acquired through a fake System Preferences dialog. Armed with the user’s credentials, the attackers would then be able to access the encrypted passwords stored within the Keychain database. While Chrome and Firefox do not store credentials in Keychain, Safari and macOS’s system service do save passwords to sites, remote file systems, encrypted drives, and other criteria resources there.
Long story short: Mac malware isn’t something to be paranoid about, but don’t lull yourself into a sense of complacency that would have you believe that it doesn’t even exist.








