iRecorder – Screen Recorder was a legitimate Android app available to download from the Google Play store. Its purpose is very clear from the name. Until August 2022, that’s all it did: let you record the screen. But an update gave iRecorder powers that turned it into a spying tool. iRecorder got the ability to use the microphone to capture audio data every 15 minutes. It also allowed the creator to download certain types of files from the phone.
After ESET researchers discovered its malware abilities, Google removed the app from the Play Store. But you might still have it installed on your Android phone and/or tablet. Therefore, you should delete it as fast as possible.
What’s puzzling about the app is the developer’s behavior. “It is rare for a developer to upload a legitimate app, wait almost a year, and then update it with malicious code,” ESET researchers wrote in a blog post.
The developer released iRecorder in September 2021. The malware-enabling update came the following August, escaping Google’s Play Store security checks. ESET says the August 2022 update was based on “the open-source AhMyth Android RAT (remote access trojan) and has been customized into what we named AhRat.”
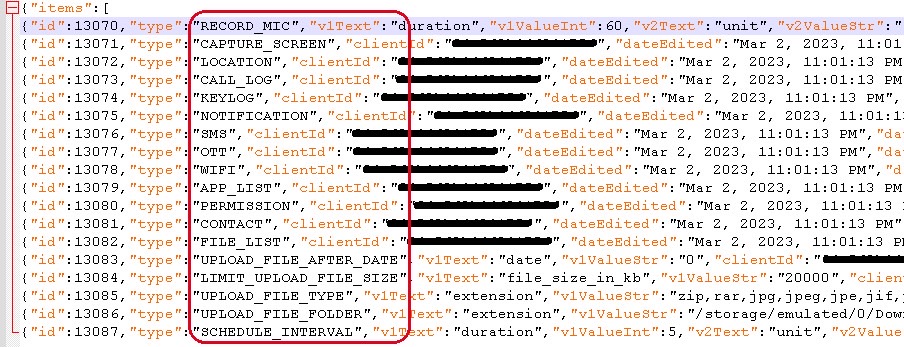
After the update, iRecorder maintained its original features. But it also got the ability to record surrounding audio from the microphone and send the files to the command and control server. The app also looked for various types of files, which it would then upload to the server. The list includes saved web pages, images, audio, video, and documents.
“The app’s specific malicious behavior – exfiltrating microphone recordings and stealing files with specific extensions – tends to suggest that it is part of an espionage campaign,” the researchers said. “However, we were not able to attribute the app to any particular malicious group.” Also, the ESET team says it hasn’t detected AhRat anywhere else.
The August update only implemented a set of potential spying features. Like extracting audio recordings and other files. But the researchers observed that other malicious features were not enabled.
iRecorder only got 50,000 downloads from the Play Store. It’s unclear who its target, or targets, might have been.
ESET points out a protective feature in Android 11, and later that might have prevented the app from spying on you. App hibernation places dormant apps into a hibernation state, resetting permissions and preventing malicious apps from working. But an app has to have been inactive for months for the protections to kick in.
Whatever the case, Google removed the malware app and all the apps that developer Coffeeholic Dev uploaded to the Play Store. Of all their apps, only iRecorder had malicious features.
If you still have iRecorder installed, you should delete it from your devices right away. Even if it’s a version that predates version 1.3.8 from last August, which quietly enabled the spying features.
If you want to discover if the app stole sensitive data from you, you might have to hire security experts for the job. Make sure you read ESET’s report as well if you think you might have been a target.







