
How Being on the Wrong Flight Turns You Into a Target for Spy Agencies
Spy agencies around the world can collect a massive amount of data from unknowing citizens in their quest to identify terror suspects, and the many Snowden …

Spy agencies around the world can collect a massive amount of data from unknowing citizens in their quest to identify terror suspects, and the many Snowden …

Stolen email and passwords belonging to individuals from nearly 50 Government agencies have leaked online, according to a CIA backed startup out of Boston. According to …

Russian antivirus company Kaspersky revealed recently that it was the target of hackers behind the Stuxnet and Duqu worms last year. The hackers have been attacking the …

Inventive researchers at Tel Aviv University have come up with a new way of spying on computer users, one that can reportedly steal passwords wirelessly …

A very serious security flaw in Apple’s iOS mobile platform and its OS X desktop operating system has been discovered by security researchers and seemingly …

A recent report from Trustwave on the state of malware relays that online crime, unfortunately, does pay. The report, originally cited by Net Security, relays …

These days, it appears as if no one is safe from hackers. Just a week after the security firm Kaspersky announced that they had been hacked …

Unknown hackers have recently hit the “PR” department of the U.S. government, stealing data for millions of employees – at least four million, according to …

Yikes. The Associated Press reports that the American Federal of Government Employees union is alleging that hackers actually stole all federal employees’ Social Security numbers in a …
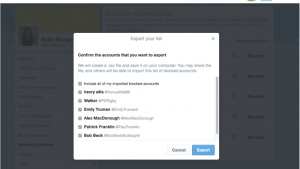
Twitter has plenty of issues, but chief among them is how easy it is for dirtbags with too much free time to berate other users. Twitter has …

Apple’s iOS platform is one of the most secure mobile operating systems in the world, and each release brings new security features and enhancements. iPhones …

A new massive data breach has been confirmed, and this time it’s not a major financial institution or retail chain hit by hackers. Instead, it’s the …
The Associated Press revealed earlier this week that the FBI appears to be the intelligence agency that’s flying spy planes in America for surveillance operations. Even …

Reports last year revealed that U.S. law enforcement agencies might have special aircraft at their disposal that masquerade as cell phone towers and collect data from the …

The old adage of, “If a product is free you are the product” isn’t lost on Apple CEO Tim Cook. During a recent speech delivered …

A security researcher has discovered a new Mac vulnerability that can seriously affect some Mac owners, even though most users should be relatively safe because the security …

An undercover operation conducted by Homeland Security Red Teams revealed that TSA security checks often do not serve their intended purpose, with airport officials failing to …

We might be entering a whole new era of malware, one where even those who lack any semblance of deep technical expertise will be able to …

If your Android phone’s performance has gotten noticeably worse, it might be because it’s being plagued by a malicious app you’ve unwittingly installed. As GreenBot …

Gulp. This isn’t good. The Associated Press reports that the Internal Revenue Service admitted on Tuesday that thieves had hacked into one of its systems and had …

A new in-depth study from Google reveals that the security questions most individuals use as an additional layer of security are often less secure and …

One of the most important things to do before selling or giving away a used smartphone is to wipe the device clean. After all, the …

In case you happen to have one or multiple adult dating website profiles, you might consider securing them right away, as one of the world’s …

Once again, we have to tip our cap in grudging admiration for the lengths the National Security Administration will go to hack into our mobile …

A potential security vulnerability recently detailed by a blogger may have uncovered a serious flaw in the Apple Watch’s design that could lead to some big headaches …

The number of tools that nefarious hackers have at their disposal these days is positively frightening. Attacks seem to be growing more complex and more dangerous …

There’s a new and depressingly simple way to steal cash from ATMs and rob other people’s bank accounts, Business Insider informs us. Apparently, thieves have started …

Verizon made headlines this week with the surprise $4.4 billion acquisition of AOL, but a new report from BuzzFeed reveals that a major security flaw …

Security researchers at Symantec recently discovered a new piece of malware that, believe it or not, incorporates a number of themes from the hit TV …

By now we’re all familiar with the upsides and downsides to the Google Play store’s approach to vetting apps: The upside is that it’s incredibly …