- Sketchy Android apps that spy on users and steal data have been a nagging presence inside Google’s Play Store for a while now, despite the search giant’s best efforts to rid its app marketplace of bad actors.
- It’s basically led to a giant game of whack-a-mole, with the latest apps to be clobbered by Google and pulled from the app store being a batch of 25 malicious apps discovered by a French cybersecurity firm.
- The apps could have stolen users’ Facebook credentials, and they racked up more than 2 million downloads.
Consider this your umpteenth reminder that for as much as Google keeps improving or promising it’s improved the company’s proprietary app marketplace, sketchy app developers will never stop coming and never stop trying to sneak into the Google Play Store — past all the company’s defenses — to put its apps into the mix and awaiting your download. Which we saw yet another example of in recent days, with the revelation that Google has booted another batch of Android apps from the store, this time 25 apps caught in a position to steal users’ Facebook login data.
Evina, a French cybersecurity firm, disclosed this news in recent weeks, with its report that a single threat group developed the batch of apps that were made to look like everything from wallpaper and flashlight apps to mobile games. However, all the apps had the same goal, as Evina explains in its report of the fraud.
“When an application is launched on your phone, the malware queries the application name,” the company explains. “If it is a Facebook application, the malware will launch a browser that loads Facebook at the same time. The browser is displayed in the foreground which makes you think that the application launched it. When you enter your credentials into this browser, the malware executes javascript to retrieve them. The malware then sends your account information to a server.”
The apps included:
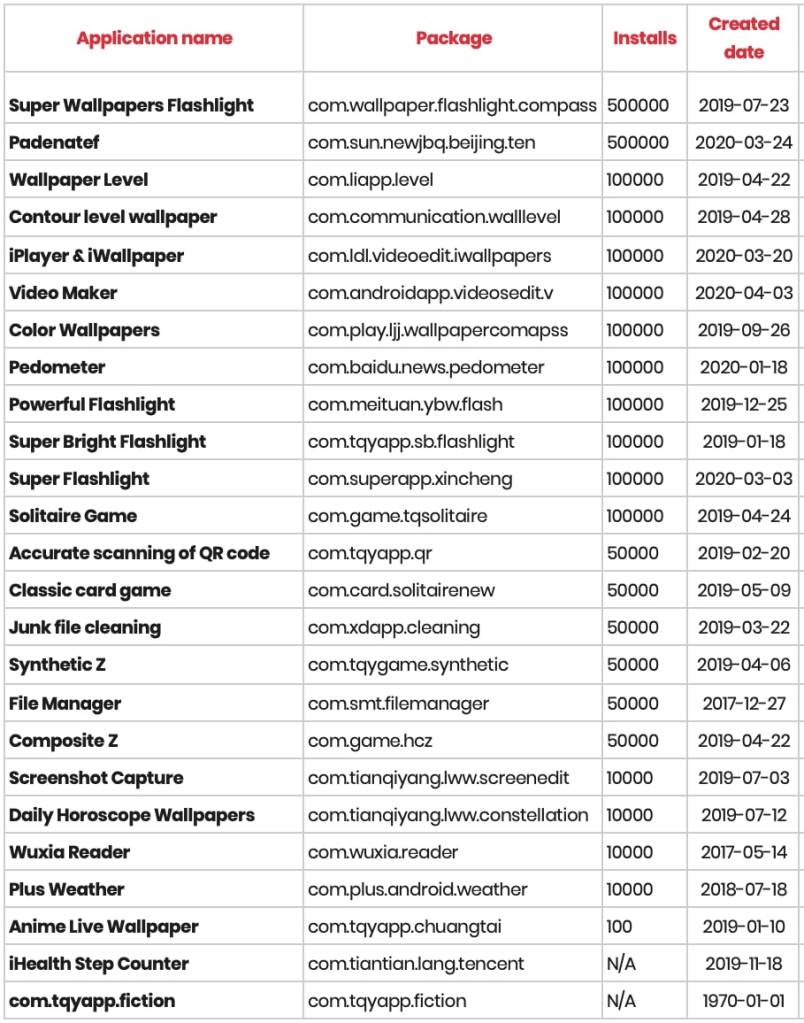
One thing to note is that when Google pulled the apps from the Play Store after Evina shared its findings, the search giant also disables the apps on the user’s end — in addition to notifying the user via the Play Store’s Play Protect service.
According to Evina, it informed Google about the apps in late May. Google investigated and took action in June, though some of the apps have been live in the Play Store since at least 2019. Cumulatively, according to the French firm, these apps garnered more than 2 million downloads.
There have been a smattering of instances like this one in recent months, such as the malware-laden group of two dozen apps (including calendar, weather, and camera functionality) that Google had to kick out of the Play Store back in February after they were found to request all sorts of potentially nefarious permissions (but not before racking up about 382 million downloads).
One of the apps, as we noted in an earlier post about this incident, was called Weather Forecast and was apparently “caught collecting user data and sending it to a server in China.”








