Late last week, security researchers uncovered what may very well be the most advanced mobile hacking tool we’ve seen to date. Dubbed Pegasus, and created by a relatively unknown Israeli company called the NSO Group, the software in question utilized three previously undisclosed iOS zero-day exploits that, in unison, managed to completely take over and surreptitiously spy on a targeted iPhone.
DON’T MISS: This stagnant technology is what’s holding Siri back
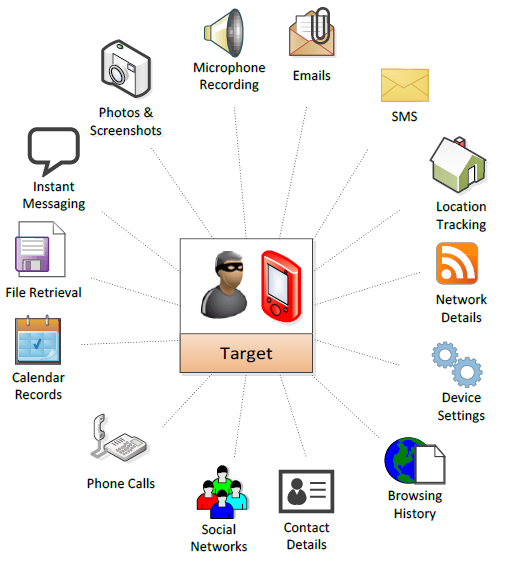
Once installed, the software is capable of eavesdropping on phone calls, text messages and a whole lot more. As evidenced via the image below — purportedly a snapshot from the NSO Group’s Pegasus documentation — Pegasus is an extremely versatile piece of spyware that can monitor all aspects of a device, including messages sent and received from iMessage, Gmail, Viber, Facebook, WhatsApp, Telegram, Skype, WeChat and more.
What makes Pegasus all the more sophisticated is that all a targeted user needs to do to unwittingly install it is to click on an SMS link. As the security group Citizen Lab notes:
According to the purported 2013 NSO Group Pegasus documentation found in the Hacking Team materials, NSO Group offers two remote installation vectors for spyware onto a target’s device: a zero-click vector, and a one-click vector. The one-click vector involves sending the target a normal SMS text message with a link to a malicious website. The malicious website contains an exploit for the web browser on the target’s device, and any other required exploits to implant the spyware. In the attack against Mansoor, the Trident exploit chain was used.
Apple was quick to issue a software patch for the security hole, but the unmasking of Pegasus helped kickstart a wave of questions regarding the identity, history and capabilities of the NSO Group.
Here’s a little bit of what we’ve learned so far.
The NSO Group is based out of Herzilya, Israel and, relative to other companies whose bread and butter centers on selling advanced software to intelligence agencies and foreign governments, it keeps a surprisingly low profile. Notably, the NSO Group doesn’t have an official online presence though its LinkedIn page does boast that it’s a “world leading company in the field of Cyber Security and research.”
Founded by Omri Lavie and Shalev Hulio in 2009, the company is said to boast a few alumni from Unit 8200, a division within the Israeli army that focuses on signals intelligence, similar in practice to the NSA.
For those curious to learn more about the NSO Group, Thomas Fox-Brewster of Forbes recently put together an engrossing list detailing everything there is to know about the company, including some of their business dealings with countries like Panama and Mexico.
NSO has close partnerships with a variety of other Israeli surveillance firms as they seek to spread their spy kit across the world. These include Ability Inc, a troubled supplier of an as-yet unproven technology called the Unlimited Interception System (ULIN). The tool exploits a crucial part of the global telecoms infrastructure known as SS7, allowing interception of calls and texts, and collection of target location, all with just a phone number, according to the firm. Of NSO, Ability founder and CEO Anatoly Hurgin told me earlier this year: “I think it’s one of the best companies in this field.” That’s something even Scott-Railton agrees with: “Pegasus is really next-level stuff.” Hurgin indicated NSO and Ability worked together, Hurgin’s team covering the network side and NSO leaving malware on devices.
One interesting albeit non-conclusive tidbit unearthed by Fox-Brewster is that one of Lavie’s LinkedIn contacts is Chaouki Bekrar. For those unfamiliar, Bekrar is the CEO of Zerodium, a company that previously offered upwards of $3 million to anyone who was able to come up with an exclusive, browser or text message-based, “workable, remote and untethered jailbreak that will persist even after reboot.”
Is Zerodium perhaps connected with the NSO Group? That might be something of a reach. Indeed, a researcher from Citizen Lab said that the NSO Group likely doesn’t need any outside assistance in developing its own wares.
“Given NSO’s public statements about their capabilities, and the size of their company, it would not be surprising to learn they’d developed their own exploits,” the researcher said.
The full-length profile on the NSO Group is well worth the read and can be viewed via the source link below.








