
Apple might be helping governments spy on users in real time
Two unrelated reports suggest that Apple might have the technical capability of mass spying on its customers in a certain area and feeding the obtained …

Two unrelated reports suggest that Apple might have the technical capability of mass spying on its customers in a certain area and feeding the obtained …

Even though the WannaCry ransomware that swept across the globe earlier this month infected more than 300,000 machines, the damage could have easily been much worse. …

Earlier this month, a piece of ransomeware known as WannaCry began spreading quickly across the globe and promptly commanded the world’s attention. Once WannaCry took …
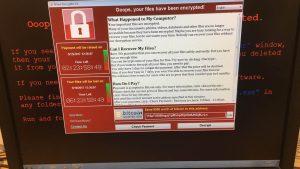
When the WannaCry ransomware took hold earlier this month, it quickly began infecting thousands of machines in a number of countries all across the world. …
Android malware is a serious problem that can cause you all kinds of trouble if you’re not paying attention to what you install on your device. Even …

The WannaCry ransomware attack took the world by surprise a few weeks ago, spreading to more than 300,000 computer systems around the world in a matter …

North Korean hackers responsible for the Sony hack in late 2014 may be behind the mid-May WannaCry ransomware attack that infected more than 300,000 computer …

A little more than a week ago, a particularly nasty piece of ransomware dubbed “WannaCry” began spreading at an impressive clip all across the globe. Targeting …

French security researchers have come up with a solution that may help users impacted by the WannaCry ransomware recover their encrypted files without having to …

At this point, it seems like every single big-name company with a web presence has been hacked at least once, and while archives of usernames …

Donald Trump still seems to dispute Russia’s meddling with last year’s US presidential elections, even if all the great intel he’s been getting says otherwise. …

Donald Trump’s desperate need to brag about something whenever he gets the chance is what got him in more trouble with the Russians. In case you …

The good news is that the “WannaCry” ransomware isn’t spreading as quickly as it was just a few days ago, in large part thanks to …

A Windows computer virus built using vulnerabilities first discovered by the NSA and stolen by hackers from the agency took the world by storm on …

As computer virus outbreaks go, the WannaCry ransomware attack currently spreading across the globe is one of the largest such attacks in some time. As …

Well, isn’t this ironic? The NSA-derived Windows malware that shook the world over the weekend may be a North Korean creation, new revelations show. That’s …

Unless you’ve taken the wise step of throwing all electronics in a dumpster and moving to a desert island, you’ve probably heard about WannaCry by …

The proliferation of the WannaCry ransomware last week unequivocally justifies Apple’s steadfast refusal to help the FBI break into an iPhone 5c used by one of …

If you’ve done your best to stay away offline for the past two days so you could actually enjoy your weekend, you undoubtedly now find yourself …

The world is facing the most dangerous cyberattack it ever had to deal with so far, and it’s an attack that it can’t be stopped …

The massive ransomware hack targeting Windows machines across the globe was stopped dead in its tracks by a security expert who inadvertently activated a “kill switch” …

Imagine that! The European Union isn’t happy with the prospect of having the US ban all laptops and tablets from carry-on luggage on flights heading …

Since early Friday morning, reports have been coming in about a massive ransomware attack sweeping through Windows PCs in Europe. The National Health Service in …

Earlier this week, Amazon announced the Echo Show — the first Echo device with a touchscreen display. Alongside that announcement, Amazon revealed that voice calling …

The UK’s National Health Service appears to have suffered a major hacking attack. Ransomware, a form of virus that encrypts personal files and then demands …

For many Windows users, Microsoft’s own built-in malware protections are the only thing standing between them and the many bad actors pushing for control of …

Back in February, we learned from a security researcher that various iOS apps can secretly leak login data and other personal information to hackers that …

When news broke that law enforcement officials in Arkansas had demanded that Amazon turn over Alexa user data that it claimed was associated with an alleged …

Yesterday, a phishing attack appeared out of nowhere to infect the inboxes of people across the world. The attack relied on a weakness in Google’s …

Intrepid hackers on Wednesday initiated a highly sophisticated Google Docs phishing attack that spread like wildfire. Using Google’s own services, the hackers were able to …