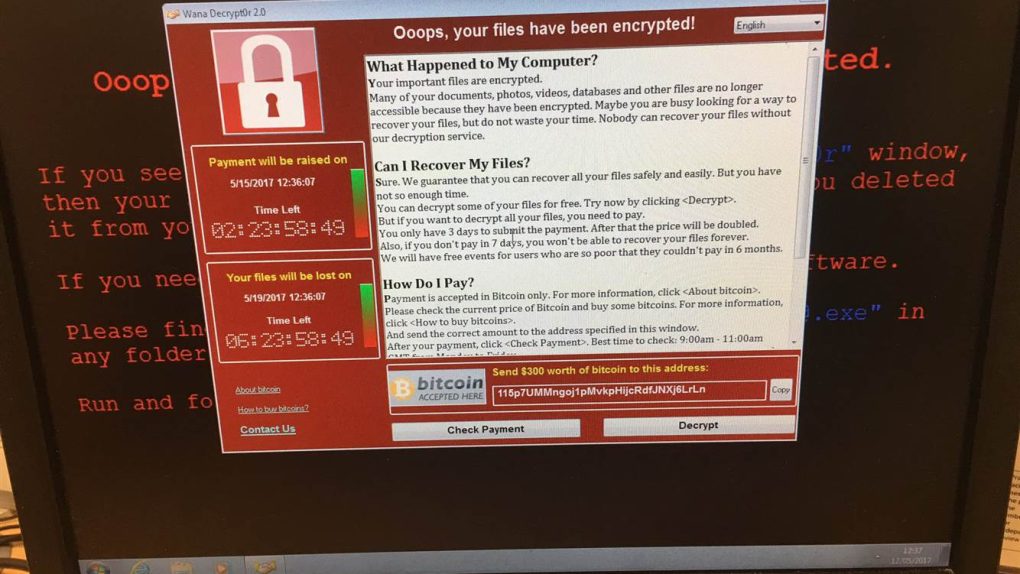
A little more than a week ago, a particularly nasty piece of ransomware dubbed “WannaCry” began spreading at an impressive clip all across the globe. Targeting Windows machines — and based off of a leaked NSA exploit — impacted users found that all of their computer files had been encrypted and could only be recovered by making a $300 payment in Bitcoin.
With the ransomware showing no signs of slowing down, an enterprising researcher named Marcus Hutchins managed to effectively stop WannaCry dead in its tracks by inadvertently enabling a kill-switch. As we noted last week, WannaCry at the point of infection attempts to communicate with a domain name consisting of a long string of nonsensical characters. If the domain is registered, WannaCry will stop spreading. If the domain is not registered, WannaCry will go on about its havoc-wreaking business.
After taking a look at the WannaCry code, Hutchins spotted an odd-looking domain name and out of mere curiosity registered it, having no idea at the time that he was enabling the ransomware’s kill-switch. Without question, Hutchins’ action here helped stopped the malware from spreading even wider, but not before it managed to infect more than 300,000 computers across the globe.
Interestingly enough, security researchers now claim that there’s a clever and concerted campaign to bring the malware back from the dead. The strategy? Taking the kill-switch domain off-line by any means necessary.
According to a report from Wired, botnets are now being mobilized to launch a DDoS attack against the kill-switch domain.
Now a few devious hackers appear to be trying to combine those two internet plagues: They’re using their own copycats of the Mirai botnet to attack WannaCry’s kill-switch. So far, researchers have managed to fight off the attacks. But in the unlikely event that the hackers succeed, the ransomware could once again start spreading unabated.
…
If the DDoS assault did succeed, not all WannaCry infections would immediately reignite. The ransomware stops scanning for new victims 24 hours after installing itself on a computer, says Matt Olney, a security researcher with Cisco’s Talos team. But anytime one of those infected machines reboots, it starts scanning again. “The ones that were successfully encrypted are in this zombie state, where they’re waiting to be reactivated if that domain goes away,” says Olney.
At this point, there’s no way of knowing if the folks behind WannaCry are the ones trying to resurrect the malware. Some security researchers, though, believe that the new botnet campaign is actually being carried out by folks looking to have a bit of ill-advised fun at the expense of innocent users.
Today's Sinkhole DDoS Attack pic.twitter.com/wxT2YUrdOF
— MalwareTech (@MalwareTechBlog) May 18, 2017
Incidentally, French security researchers have since come up with a fix for the WannaCry ransomware called ‘wannakiwi’ that can be downloaded here.