If you’ve done your best to stay away offline for the past two days so you could actually enjoy your weekend, you undoubtedly now find yourself trying to catch up on all the news surrounding WannaCry ransomware. This unprecedented malware attack began sweeping the globe late last week, and security researchers estimated that nearly 57,000 computers in more than 150 countries were infected by the end of the day on Friday. While the spread of this terrifying ransomware was slowed on Saturday, it was hardly stopped. As of Monday morning, more than 200,000 systems around the world are believed to have been infected.
WannaCry is far and away the most severe malware attack so far in 2017, and the spread of this troubling ransomware is far from over. In this post, we’ll tell you what WannaCry is, what developments we’ve seen over the past three days, and how to protect yourself.
What is WannaCry?
First and foremost, let’s clarify exactly what WannaCry is. This malware is a scary type of trojan virus called “ransomware.” As the name suggests, the virus in effect holds the infected computer hostage and demands that the victim pay a ransom in order to regain access to the files on his or her computer.
What exactly does WannaCry do?
RansomWare like WannaCry works by encrypting most or even all of the files on a user’s computer. Then, the software demands that a ransom be paid in order to have the files decrypted. In the case of WannaCry specifically, the software demands that the victim pays a ransom of $300 in bitcoins at the time of infection. If the user doesn’t pay the ransom without three days, the amount doubles to $600. After seven days without payment, WannaCry will delete all of the encrypted files and all data will be lost.
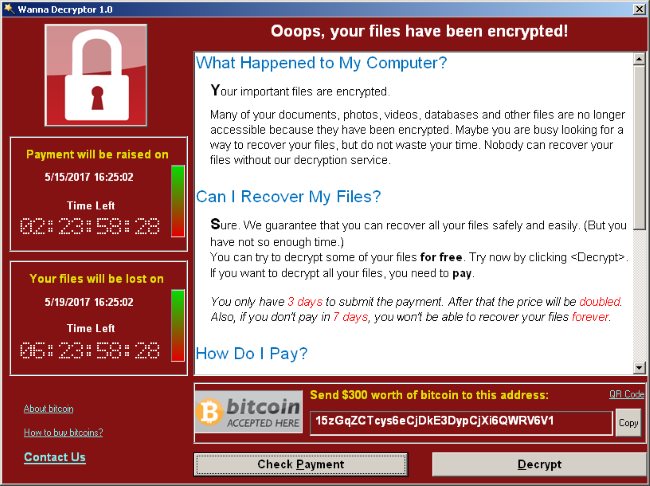
Per Symantec, here is a full list of the filetypes that are targeted and encrypted by WannaCry:
- .123
- .3dm
- .3ds
- .3g2
- .3gp
- .602
- .7z
- .ARC
- .PAQ
- .accdb
- .aes
- .ai
- .asc
- .asf
- .asm
- .asp
- .avi
- .backup
- .bak
- .bat
- .bmp
- .brd
- .bz2
- .cgm
- .class
- .cmd
- .cpp
- .crt
- .cs
- .csr
- .csv
- .db
- .dbf
- .dch
- .der
- .dif
- .dip
- .djvu
- .doc
- .docb
- .docm
- .docx
- .dot
- .dotm
- .dotx
- .dwg
- .edb
- .eml
- .fla
- .flv
- .frm
- .gif
- .gpg
- .gz
- .hwp
- .ibd
- .iso
- .jar
- .java
- .jpeg
- .jpg
- .js
- .jsp
- .key
- .lay
- .lay6
- .ldf
- .m3u
- .m4u
- .max
- .mdb
- .mdf
- .mid
- .mkv
- .mml
- .mov
- .mp3
- .mp4
- .mpeg
- .mpg
- .msg
- .myd
- .myi
- .nef
- .odb
- .odg
- .odp
- .ods
- .odt
- .onetoc2
- .ost
- .otg
- .otp
- .ots
- .ott
- .p12
- .pas
- .pem
- .pfx
- .php
- .pl
- .png
- .pot
- .potm
- .potx
- .ppam
- .pps
- .ppsm
- .ppsx
- .ppt
- .pptm
- .pptx
- .ps1
- .psd
- .pst
- .rar
- .raw
- .rb
- .rtf
- .sch
- .sh
- .sldm
- .sldx
- .slk
- .sln
- .snt
- .sql
- .sqlite3
- .sqlitedb
- .stc
- .std
- .sti
- .stw
- .suo
- .svg
- .swf
- .sxc
- .sxd
- .sxi
- .sxm
- .sxw
- .tar
- .tbk
- .tgz
- .tif
- .tiff
- .txt
- .uop
- .uot
- .vb
- .vbs
- .vcd
- .vdi
- .vmdk
- .vmx
- .vob
- .vsd
- .vsdx
- .wav
- .wb2
- .wk1
- .wks
- .wma
- .wmv
- .xlc
- .xlm
- .xls
- .xlsb
- .xlsm
- .xlsx
- .xlt
- .xltm
- .xltx
- .xlw
- .zip
As you can see, the ransomware covers nearly any important file type a user might have on his or her computer. It also installs a text file on the user’s desktop with the following ransom note:
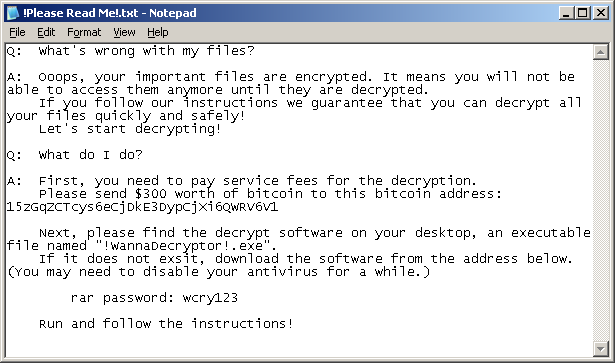
How was WannaCry created?
You can thank the NSA for discovering the “EternalBlue” exploit that would later be used by the WannaCry trojan, and then for keeping under wraps to use for its own intelligence gathering purposes. The security hole was then made public last month when a group of hackers called Shadow Brokers released the details of the exploit to the public.
Is the attack over?
No.
WannaCry was first discovered on Friday, May 12th, and it had spread to an estimated 57,000 computers in more than 150 different countries around the world by the end of the day. European countries were hit the hardest, and business ground to a halt at several large companies and organizations, including banks, hospitals, and government agencies.
On Saturday, a 22-year-old security researcher named Marcus Hutchins inadvertently slowed the spread of the WannaCry virus when he registered a domain name hidden within the virus’ code in an attempt to track the spread of WannaCry, unintentionally stopping its progress in the process. You can read Hutchins’ story in his blog post titled “How to Accidentally Stop a Global Cyber Attacks.”
Unfortunately, the spread of WannaCry wasn’t actually stopped, but instead slowed.
How can I protect myself from WannaCry?
Regardless of which operating system you run, you should install any and all available security updates immediately. Specifically, Windows users with machines that run Windows XP, Windows 8, or Windows Server 2003 should immediately install this security update released on Friday by Microsoft.
What can I do if my computer is infected with WannaCry?
Sadly, there is no confirmed fix for WannaCry available at this time. Antivirus companies and cybersecurity experts are hard at work looking for ways to decrypt files on infected computers, but no means of third-party decryption are available right now. Hopefully affected users have backups of their data available, because the only other option right now that is known to work is to follow the instructions offered in the software to pay the ransom. Bleeping Computer has a WannaCry decryption guide on its site, but we cannot confirm whether or not it’s effective.








