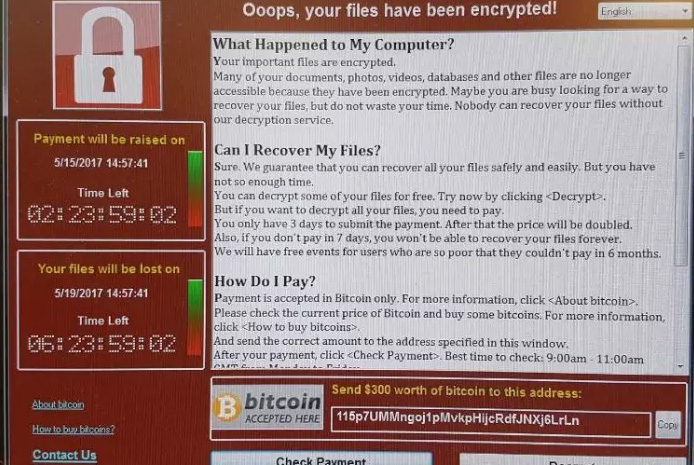
Just over a month ago, a nasty piece of ransomware called “WannaCry” began infecting PCs all across the world at an alarming rate. Based off of a leaked NSA exploit, the malware worked by encrypting all of a user’s files and offering up a decryption key only upon receipt of a $300 payment via Bitcoin. In the span of just a few days, WannaCry managed to infect nearly 300,000 machines, a tally which could have been much higher had it not been for a researcher who inadvertently activated WannaCry’s kill-switch.
As it turns out, WannaCry hasn’t been completely thwarted as previously believed. According to reports, the malware infected the computer system at one of Honda’s manufacturing plants in Japan earlier this week, leading to a complete plant shutdown this past Wednesday.
Honda discovered on Sunday that the virus had affected networks across Japan, North America, Europe, China and other regions, a spokeswoman said, despite efforts to secure its systems in mid-May when the virus caused widespread disruption at plants, hospitals and shops worldwide.
The impacted plant is reportedly back up and running.
In the midst of the WannaCry saga, many folks were quick to blame Windows XP for the ransomware’s impressive ability to rapidly infect machines. But as it was later discovered, nearly all of the machines impacted by WannaCry — to the tune of 98% — were running a variant of Windows 7.
The sad reality of this whole saga is that WannaCry may simply be the start of much more damaging malware campaigns. Recall, the hacker group responsible for leaking the NSA exploit upon which WannaCry was based — an entity known as the Shadow Brokers — has said that it has many more exploits that it will make available to anyone willing to pay.
Most recently, the British National Cyber Security Centre has found links, albeit circumstantial, between the WannaCry ransomware and North Korea.