This Clever Netflix Scam Attempts To Steal Your Credit Card Information
- A new Netflix phishing scam has been making the rounds that attempts to steal your login and credit card information by tricking you into updating your account.
- The scam directs users to a surprisingly convincing Netflix clone site to enter their details.
- Always be sure to triple check the sender before you click a link inside of any email you receive.
The internet is a dangerous place. By now, many of us are savvy enough to avoid the most obvious scams and ploys online, but much like a mutating virus, this forces the bad actors to adapt. As a result, scams become even harder to detect, which is why it's so important to be diligent when visiting websites or opening emails that look suspicious. To that point, cloud office security platform Armorblox published a blog post this week detailing a new Netflix phishing attack that seeks to steal your login credentials, billing address, and credit card details.
Armorblox first spotted the phishing attack a few weeks ago when Netflix customers started receiving emails in their inboxes that claimed to be from Netflix Support. The email informed the customers that there was a problem verifying their personal details and that it was resulting in billing issues. They were also told their accounts would be canceled in 24 hours if they didn't update their personal information to solve the problem.
"When targets clicked the link, they were led to a fully fledged Netflix lookalike website with a phishing flow that asked them to part with their Netflix login credentials, billing address, and credit card details," Armorblox co-founder Chetan Anand explained in the blog post. "Once the phishing flow was complete, targets were redirected to the real Netflix home page, none the wiser about being compromised."
Email phishing attacks are a dime a dozen, but as Armorblox explains, this one was noteworthy because it was able to get through email security controls. The first trick that the hackers used was redirecting users to "a fully functioning CAPTCHA page with subtle Netflix branding" if they clicked the link in the email. This made the entire procedure look more legitimate, and might have been enough to convince some Netflix customers.
Furthermore, both the CAPTCHA page and the Netflix clone site were hosted on legitimate domains, one of which belongs to Wyoming Health Fairs and the other of which is hosted on the site of an oil and gas company in Texas. "By hosting phishing pages on legitimate parent domains, attackers are able to evade security controls based on URL/link protection and get past filters that block known bad domains," Anand says.
Finally, the Netflix clone site itself, which you can see below, really does look like the real Netflix login page. It even has a few extraneous flourishes, like a "Need help?" link and the option to login with Facebook (though these extra links just reload the same page — they aren't actually functional if you click on them):
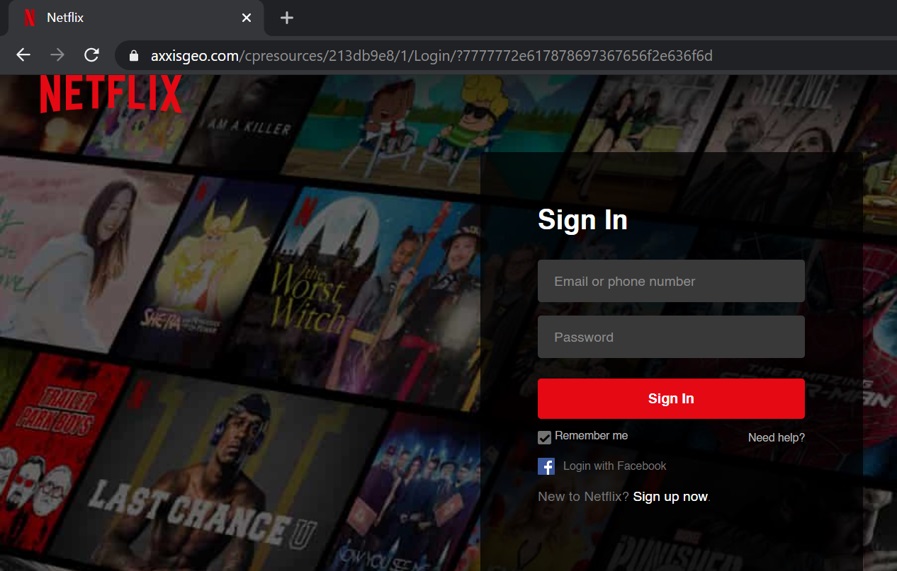
Whether or not you would have fallen for this scam, it never hurts to know what's out there. After all, if that email had managed to get through into your inbox, there's a chance you could have given away your personal information and credit card number. That said, as clever as this attack might have been relative to the spam you ignore every day, detecting it would have been as simple as looking at the address bar in your browser.
