Beware Of Hackers And Scams When You're Installing Meltdown And Spectre Patches
Last week, the world learned that most computers and smartphones out there contain chips that come with severe hardware flaws that would allow hackers to target users with apps that easily extract highly sensitive data like passwords. Intel, AMD, and ARM chips are all impacted by the Meltdown and Spectre security threats, and the processors can't be fixed or replaced.
Instead, chipmakers, device makers, and software companies have come up with all sorts of updates meant to safeguard computers and smartphones against malware apps that would try to take advantage of Meltdown-Spectre.
But some hackers were quick to create malware that's meant to take advantage of your Meltdown-Spectre fears. The malicious app is disguised as a patch supposed to protect your computer against the chip flaws.
The problem with the Meltdown and Spectre patches that were released so far is that they're not all bug-free. Furthermore, you can expect device makers to issue successive updates to affected computers, especially the ones that developed various side-effects after the initial wave of Meltdown-Spectre patches.
Ingenious hackers, meanwhile, created Meltdown-Spectre attacks, targeting unsuspecting users with links that actually download malicious apps on their machines.
The first case has been discovered in Germany, ZDNet reports, where the Federal Office for Information Security (BSI) issued a formal alrert detailing spam messages that impersonate the agency. The phishing emails appear to come from BSI, and they're looking to convince users to click on malicious links that download malware.
"The Federal Office for Information Security (BSI) is not the sender of these emails," the notice reads. "Recipients of such or similar emails should not click on links or any attached documents, but instead delete the email. Users who have opened the fake website should never download the alleged security update linked there."
Malwarebytes has identified one of the pages the spam emails were pointing to, as BSI did not actually list those sites. Interestingly, these pages come with HTTPS protection, an element supposed to further convince users they're looking at a genuine BSI document.
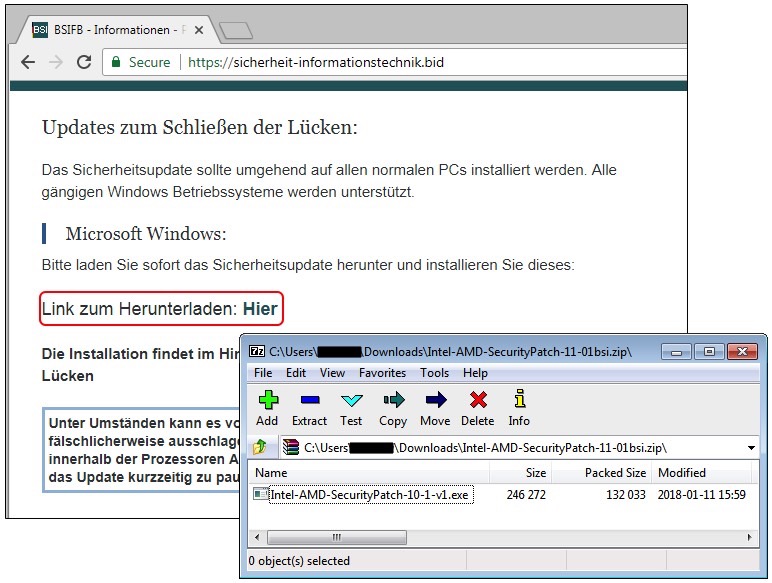
The fake pages prompt the user to download an executable Windows program, as seen above, which will install the malicious app, called Smoke Loader. In turn, the loader would install other payloads from various domains in Russia — read more about the newly discovered threat at this link.
The best way to go about Meltdown-Spectre updates is to read official notifications from chipmakers (Intel, AMD, ARM), software makers (Apple, Google, Linux, Microsoft), and device makers. Whatever you do, don't click on links in unsolicited emails that may be hitting your inboxes these days.
Actual threats that take advantage of the Meltdown-Spectre flaws are yet to be identified — or nobody is willing to detail them if they already exist.
