iOS Might Have A Backdoor That Can Be Used To Hack Into Any iPhone, Even The iPhone X
Apple has been advertising its focus on user data security and privacy for years now. Encryption ensures data security as long as you protect your devices with a password, pin, fingerprint, or face. Nobody should be able to access the contents of your iPhone without access to your password, and that's why the FBI tried to force Apple in early 2016 to create a backdoor into an iPhone belonging to the San Bernardino shooters.
Ultimately, the FBI backed down because it discovered it could use a third-party's services to access the password-protected iPhone. In other words, someone found a backdoor into Apple's 2016 software and was able to use it to access the contents of encrypted iPhones. Fast forward to 2018, and it looks like a similar backdoor still exists and can unlock encrypted any device, including the iPhone X.
The device in the following image looks like an Apple TV, but it is, in fact, a gadget that can decrypt iPhones. It's called GrayKey, first detailed in a blog post on Malwarebytes, and features two Lightning cables.

Two phones can be connected for about two minutes. After that, they're disconnected, and the cracking begins. It all happens on the phone, as some sort of software is loaded on it using the GrayKey box. The software, which seems to jailbreak the phone, brute-forces its way into the password.
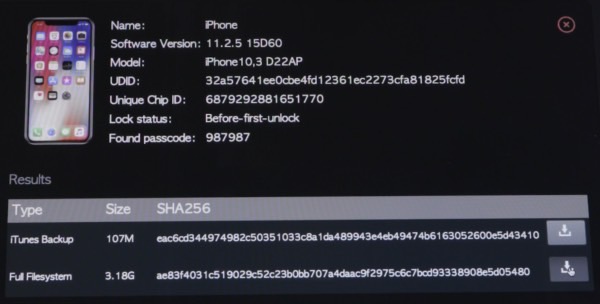
After a period of time, the iPhone will show a black screen that contains the password needed to decrypt the phone. The company that makes these boxes is called Grayshift and claims that even disabled phones can be unlocked.

Once the password is obtained, the full contents of the phone are downloaded to the GrayKey device. That includes the entire unencrypted contents of the keychain.
The following image shows that no iPhone is safe. An iPhone X running iOS 11.2.5 was hacked using the same hardware.
Malwarebytes explains that GrayKey comes in two flavors, including a $15,000 option that requires an internet connection and is geofenced to a single location. The $30,000 model will let you use the GrayKey without an internet connection, and you can move the device anywhere you want.
It's unclear whether the iOS vulnerabilities used to crack the San Bernardino iPhone are what make possible these GrayKey hacks. Grayshift was founded in 2016, and it sells the device to law enforcement agencies. But if this report is accurate and the gadget can break into Apple's latest iOS release, it doesn't even matter. The fact remains that someone out there found a way to bypass Apple's encryption, a backdoor that can be exploited for as long as it takes for Apple to patch it.
As long as only law enforcement uses these devices, you should not worry too much about it. But if obtained by malicious individuals, GrayKey may be used to spy on people — physical access to the device is still needed. And you can imagine how happy totalitarian regimes out there would be to find out they can spy on encrypted iPhones. What's worse, the device could help iPhone thieves reset stolen iPhones that are locked with a password and then sell them.
It goes without saying that it's very unlikely that Apple built this backdoor into iOS. And if it did, we'd never know that such a backdoor officially exists. That's the point of backdoors. But the fact that someone not connected to Apple was able to unearth this vulnerability proves, once again, why backdoors should not be built into encrypted devices. Eventually, someone out there will dig them up.
