How To Fix The Google Docs Scam If You've Already Been Hacked
There's an incredibly dangerous Google Docs phishing scam sweeping through the internet today. It uses Google's own Apps system to compromise email accounts, so thousands of users are falling victim to it.
You can read our original post on how it works and how to avoid it, but that doesn't really help if you've already clicked the link. Here's how to fix the Google Doc hack, for anyone already compromised.
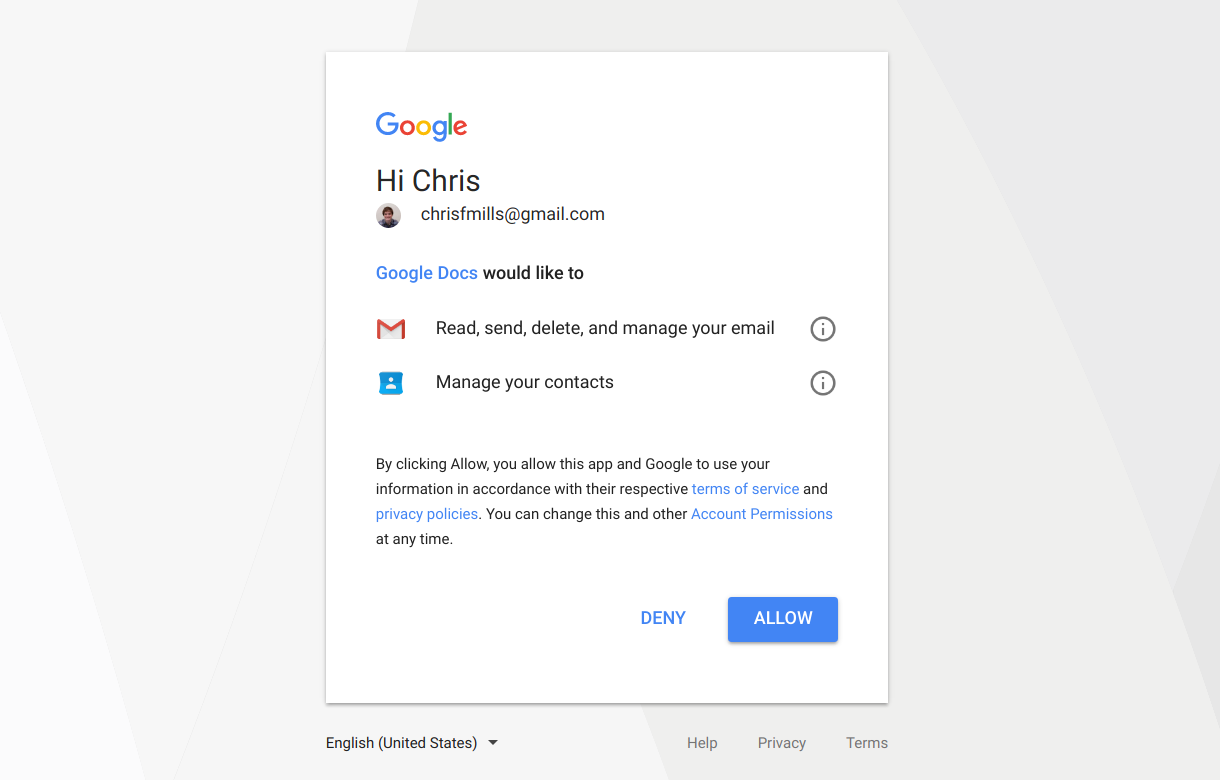
The Docs attack works by tricking you into authorising a fake app, called "Google Docs," and allowing it to read, send and delete your emails. The kind of damage a hacker can do with that access is huge: most of your other accounts probably use Gmail as the "reset account" email, so it would theoretically let a hacker get control of your Apple, Amazon, Facebook and Twitter accounts — just for starters.
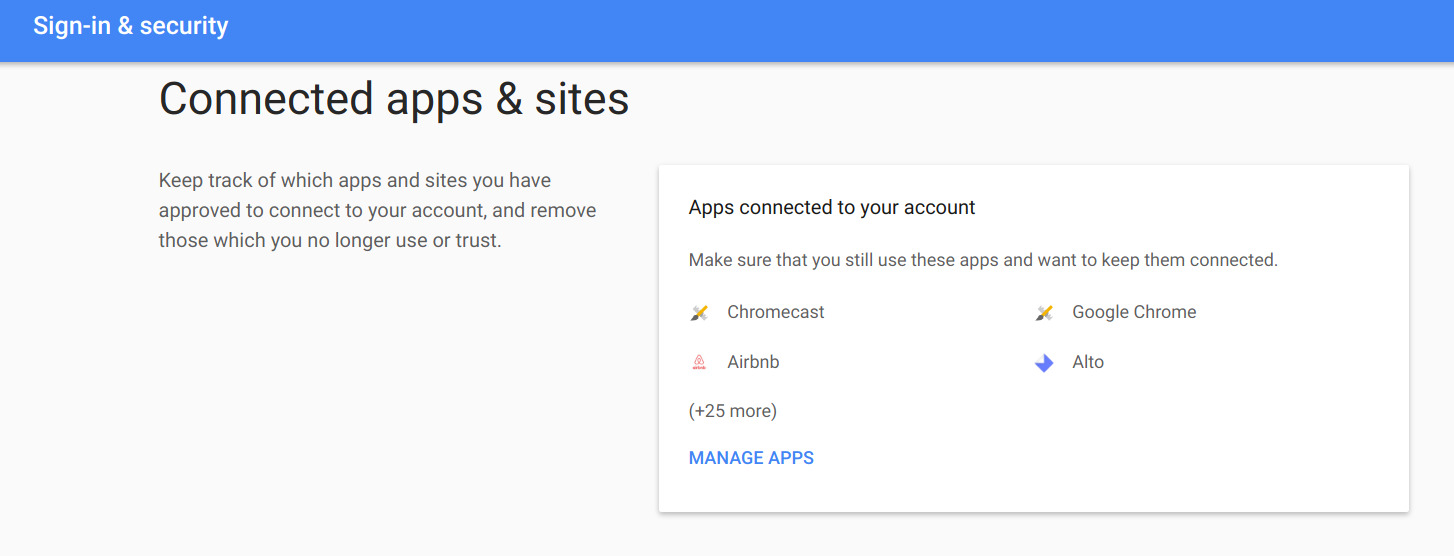
Luckily, because the hack uses Google's own Apps system to gain control, it's also easy to delete. Go to Google's account management page, Sign-In and Security, and then Connected Apps. Once you're there, hit the button that says "Manage Apps" to see the full list of apps and permissions.
You're looking for one titled "Google Docs," but this is a good opportunity to go through the list and delete anything you don't recognize, or anything with permissions that are far too broad. Google is already taking steps to fix this attack, so if you don't see the Google Docs app in the list, it means you're probably safe.
This attack was unusual for using Google's own Apps framework to target users, but emails with links are not an unusual way to hack users. Nimrod Vax, the co-founder of security firm BigID and an expert on phishing attacks, described it as a "classic spear-phishing attack" that "works because it looks familiar."
Going forward, he suggests using this opportunity to "really look at what permissions an app is asking for" — using Google's account system was clever, but if you "look at permissions before you authorize an app, you can see what if what they're asking for is unusual. There's no reason a PDF reader would need to read and delete emails."