Bloomberg Reports Bombshell Chinese Hardware Attack On US Tech Companies, Met With Swift Denials
A bombshell report claims that China has been developing a massive spying operation for a few years that involved building hardware backdoors into critical server components with the help of microchips no bigger than a grain of rice or the tip of a sharpened pencil. Those chips, once placed on motherboards that go into popular servers, would be able to help Chinese spies access information that would otherwise be unavailable to them.
The in-depth expose comes from Bloomberg Businessweek, which cited up to 17 people with knowledge of the hardware manipulation, including six current and former national security officials, as well as sources from Amazon's AWS business and three Apple insiders. The report notes that at least 30 US companies may have been victimized by the supply chain hardware hack, including prominent names like Amazon and Apple.
Amazon, Apple, and Supermicro have all denied the allegations, as has China.
Altering the hardware would give attackers immense power over the software, the report explains. The chips would be able to connect to outside computers and force the hardware to allow more malware to be installed:
This system could let the attackers alter how the device functioned, line by line, however they wanted, leaving no one the wiser. To understand the power that would give them, take this hypothetical example: Somewhere in the Linux operating system, which runs in many servers, is code that authorizes a user by verifying a typed password against a stored encrypted one. An implanted chip can alter part of that code so the server won't check for a password—and presto! A secure machine is open to any and all users. A chip can also steal encryption keys for secure communications, block security updates that would neutralize the attack, and open up new pathways to the internet.
The hardware hack would give attackers unprecedented access to US companies and the government with little risk of discovery. One malicious chip reportedly found in AWS servers in China was so small that it would fit between the layers of fiberglass on which the other components were attached.
Bloomberg offers this animation to highlight the size of the chip relative to the motherboard:
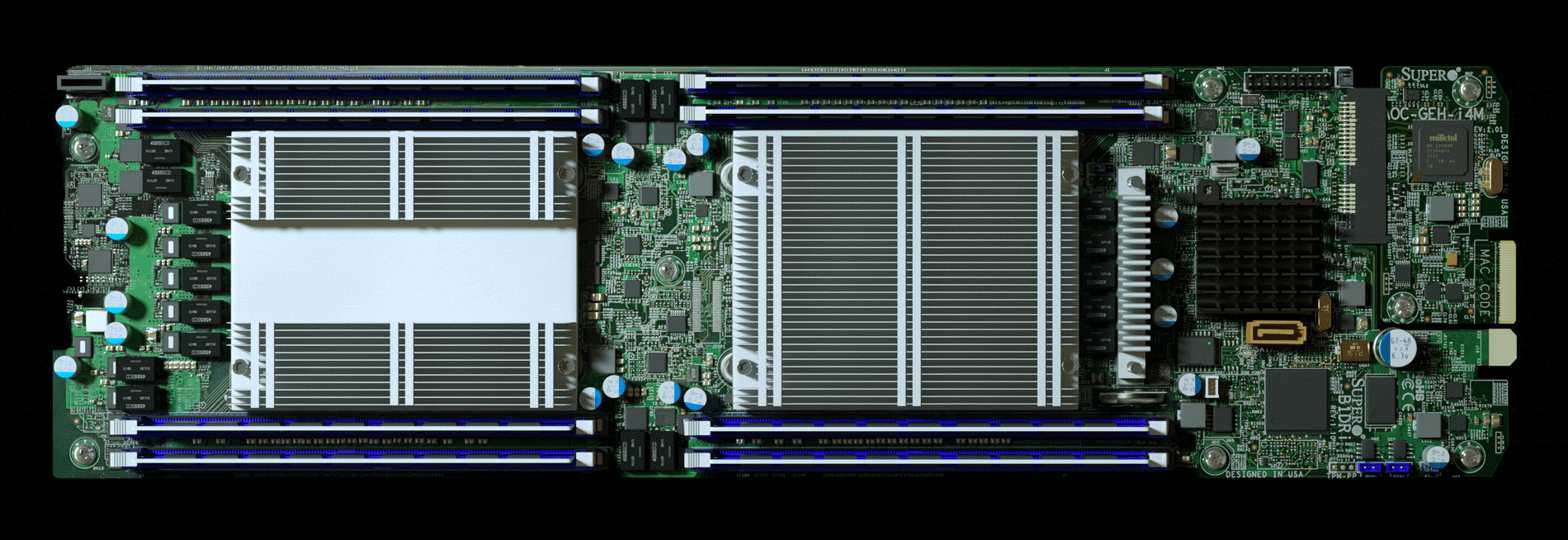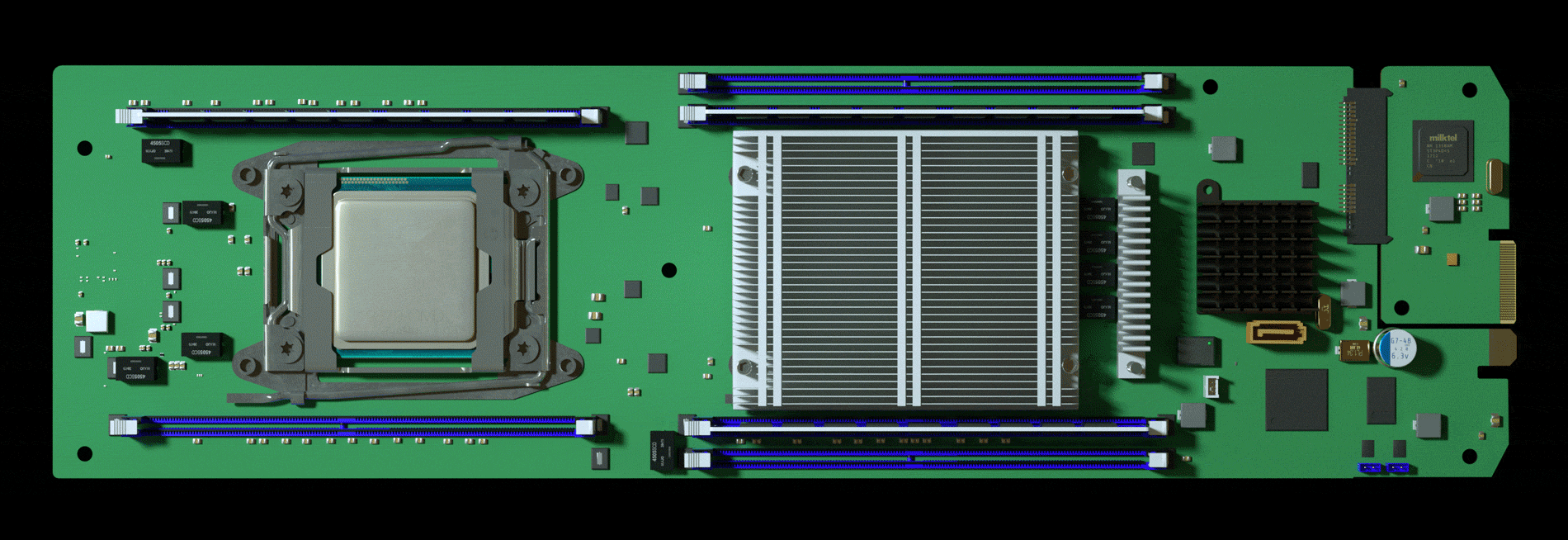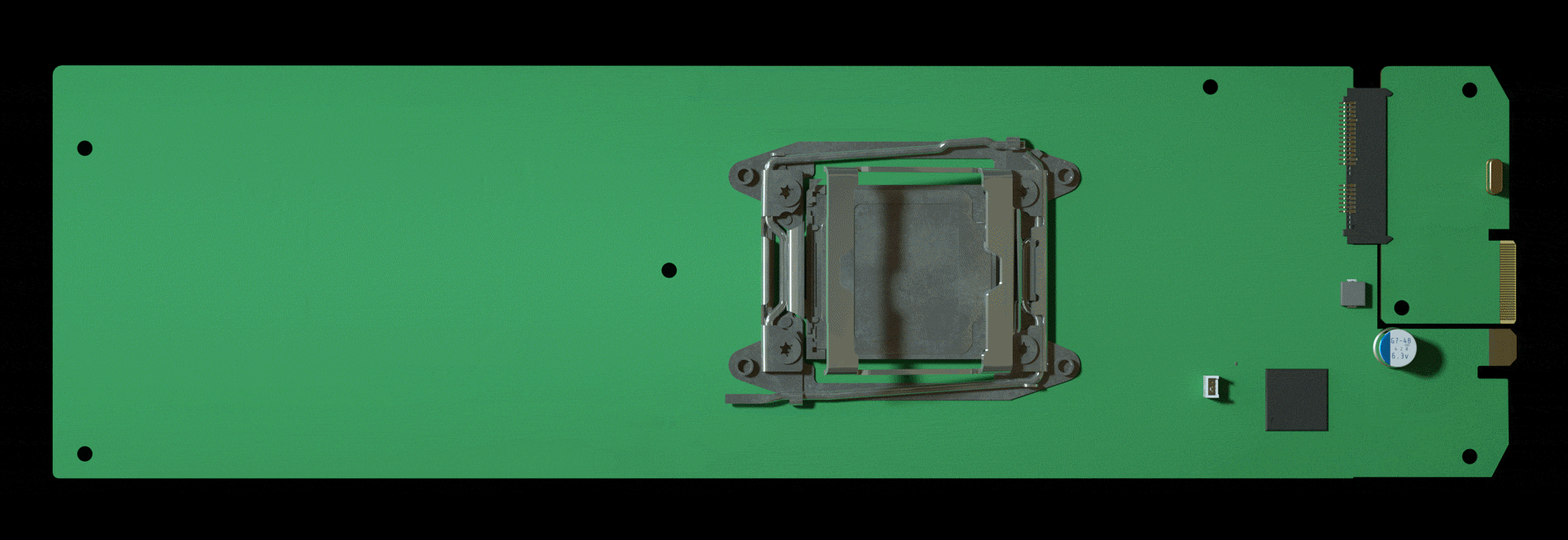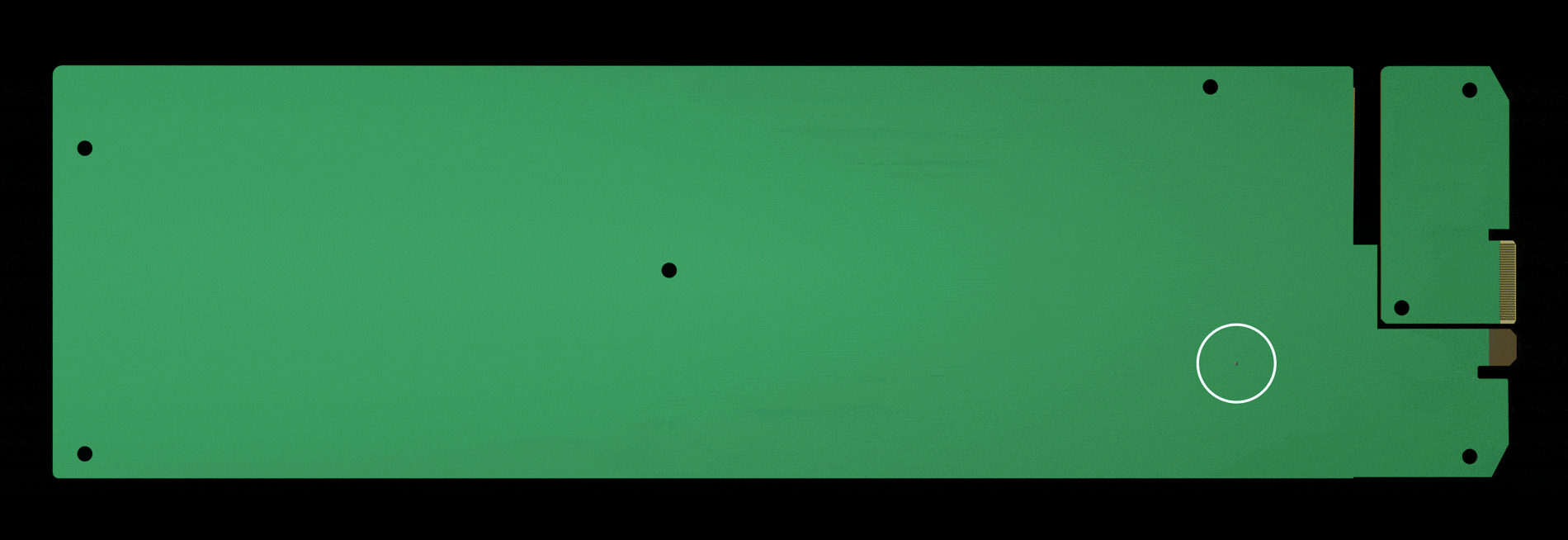
According to Bloomberg, for Amazon it all started in 2015, when it hired a third-party security team to look into Elemental's hardware. The team then apparently discovered a tiny microchip that wasn't bigger than a grain of rice on motherboards from Elemental, hardware that was built by Supermicro. Amazon then is said to have relayed the information to the US government. Elemental servers were also present in Department of Defense data centers, CIA drone operations, and Navy warships.
Amazon denied all allegations:
It's untrue that AWS knew about a supply chain compromise, an issue with malicious chips, or hardware modifications when acquiring Elemental. (Amazon's full denial to Bloomberg is available here.)
In May of the same year, Apple discovered unusual network activity and firmware problems and found suspicious chips inside Supermicro servers. The FBI was notified, but Apple did not allow investigators inside its data centers. In the months that followed, Apple replaced Supermicro servers and cut ties with the company, in spite of earlier plans to increase the number of Supermicro servers in its data centers.
Apple also denied all allegations:
On this we can be very clear: Apple has never found malicious chips, 'hardware manipulations' or vulnerabilities purposely planted in any server. (Apple's full denial to Bloomberg is available here.)
We are deeply disappointed that in their dealings with us, Bloomberg's reporters have not been open to the possibility that they or their sources might be wrong or misinformed. Our best guess is that they are confusing their story with a previously reported 2016 incident in which we discovered an infected driver on a single Super Micro server in one of our labs. That one-time event was determined to be accidental and not a targeted attack against Apple. (Apple's denial to CNBC.)
Here's how big an alleged malicious chip is, compared to a penny:

For the US government, it all started even earlier. Intelligence sources noted that China wanted to introduce microchips into the supply chain well before the discoveries made by Amazon and Apple, Bloomberg reports. In the first half of 2014, the White House learned that it was Supermicro motherboards bound for US companies that China's military was targeting. From there, US intelligence went hunting for the culprits, and found the Chinese suppliers responsible for the alteration of the original motherboard designs:
They [US spies] sifted through communications intercepts, tapped informants in Taiwan and China, even tracked critical individuals through their phones, according to the person briefed on evidence gathered during the probe. Eventually, that person says, they traced the malicious chips to four subcontracting factories that had been building Supermicro motherboards for at least two years.
"Think of Supermicro as the Microsoft of the hardware world," says a former U.S. intelligence official who's studied Supermicro and its business model. "Attacking Supermicro motherboards is like attacking Windows. It's like attacking the whole world."
Supermicro also issued a denial:
We remain unaware of any such investigation. (Supermicro's full denial to Bloomberg is available here).
After discovering the servers these chips were interacting with, US intelligence agencies hacked those computers, and concluded that almost 30 companies used tainted hardware, though there could be more.
But rather than accusing an American company, Supermicro, of selling hardware that was tampered with during production without its knowledge, officials reached out to some of its most important customers, signaling that Supermicro couldn't be trusted. The object of the game for China wasn't the theft of personal customer data (incidents that were not observed according to a US official). Instead, China wanted direct access to high-value corporate secrets and sensitive government networks.
In the weeks that followed a September 2015 cybersecurity deal between the US and China, the US government briefed several dozen tech executives and investors during an invite-only Pentagon meeting in McLean, Va. on a recent attack, advising them to create commercial products that could detect hardware implants. Supermicro's name wasn't mentioned, but to some people, it was clear who they were referring to.
China denied the allegations:
China is a resolute defender of cybersecurity.
We hope parties make less gratuitous accusations and suspicions but conduct more constructive talk and collaboration so that we can work together in building a peaceful, safe, open, cooperative and orderly cyberspace. (China's full denial to Bloomberg is available here).
Bloomberg says that the matter is still ongoing. In the three years since that meeting, no commercial product to detect hardware backdoors has emerged. "This stuff is at the cutting edge of the cutting edge, and there is no easy technological solution," one of the people present in McLean says. "You have to invest in things that the world wants. You cannot invest in things that the world is not ready to accept yet."
China may deny its involvement in this type of cyber attack, but it'd be hardly the only nation-state capable of such endeavors. Reports back in 2013, when Snowden leaks were in fashion, said that the US intelligence agencies would routinely intercept hardware and implant bugs before the goods were delivered to customers.
