A few months back, we covered a nasty and incredibly advanced piece of malware dubbed Pegasus. Created by a relatively obscure Israeli security company called the NSO Group, Pegasus seemingly set a new bar for mobile hacking sophistication. Built upon three previously undisclosed iOS zero-day exploits, Pegasus, once installed, was able to eavesdrop on conversations, remotely spy on a users’s text messages, location, browsing history, calendar records, photos and more.
Apple has since patched the aforementioned zero-day exploits, but an Android variant of Pegasus has since been discovered by security researchers from Google and Lookout and, believe it or not, it’s even more dangerous than the original.
The Android version of Pegasus is being called Chrysaor and, not surprisingly, houses an extensive list of surveillance features similar to the list above, along with some other goodies such as keylogging, live audio capture and more. Additionally, Chrysaor has the ability to spy on all types of popular messaging apps, including WhatsApp, Twitter, Skype and Facebook.
What makes Chrysaor more worrisome than Pegasus, however, is that it doesn’t rely on zero-day exploits in order to infect a targeted device. In effect, it’s a lot easier to infect an Android device with Chrysaor than it was to infect an iOS device with Pegasus.
Pegasus for Android does not require zero-day vulnerabilities to root the target device and install the malware. Instead, the threat uses an otherwise well-known rooting technique called Framaroot. In the case of Pegasus for iOS, if the zero-day attack execution failed to jailbreak the device, the attack sequence failed overall. In the Android version, however, the attackers built in functionality that would allow Pegasus for Android to still ask for permissions that would then allow it to access and exfiltrate data. The failsafe jumps into action if the initial attempt to root the device fails.
This means Pegasus for Android is easier to deploy on devices and has the ability to move laterally if the first attempt to hijack the device fails.
Speaking to the sophistication of the malware, security researches also discovered that Chrysaor is designed to self-destruct any time there’s a possibility it may be discovered. Lookout notes that a self-destruct mode will initiate in a handful of circumstances, such as if the SIM MCC ID is invalid or if an infected device has not checked “in with the servers after 60 days.”
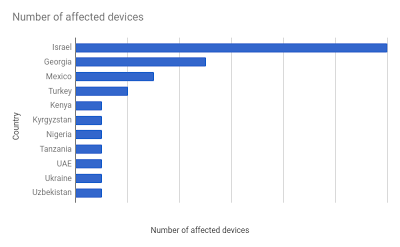
As for where compromised devices were found, Google today published the following chart while noting that it unearthed an extremely small number of installs. Google’s chart doesn’t list any specific figures, but the search giant claims that it “observed fewer than 3 dozen installs of Chrysaor on victim devices.”
Notably, no apps on the Google Play store were found to contain Chrysaor. So, as always, Android users would be well-advised to play it safe and avoid downloading apps from third-party sites.








